Decoding or understanding to read email headers and its contents can help us troubleshoot multiple email related issues.
Whenever we open any email, we tend to look at the sender, subject and the body of the email. But emails hold much more information beyond these elements.
The email headers also indicate where the email was created, when it was received, the servers through which the email was routed (routing details), and many other details about the email.
Table of contents
How to view the email headers of any email.
- Outlook for Windows: Double-click an email message –> File > Properties –> Header information appears in the Internet headers box.
- New Outlook and Outlook on the Web: Select the email –> select the ( … ) option –> View –> View message details.
- Gmail: open Gmail (from browser) –> Select / Open the email –> Next to Reply , click More More –> Show original.
NOTE: View the email headers from the recipient’s mailbox of the email. If you try to check the email header from sender sent items in Microsoft 365, it will usually show up as empty but it shows few details for sender, from sent items of Gmail mailbox.
Once you view the email headers, Select all the email headers and copy it (ctrl + c) and use any of the below websites to check the details of email headers.
Sites that you can use to check email headers.
Many websites on the internet allow users to check email headers; below are a few of them.
- Microsoft Message Header Analyzer
- MX Toolbox Email Header Analyzer
- Google Admin Toolbox Message header Analyzer
Open any of the above website, paste the copied header and select Analyze Headers button on the webpage.
Details of the email header fields.
For demonstration, I have sent the email from Gmail user to the recipient in Microsoft 365. I have collected the email headers from the Microsoft 365 hosted mailbox.
Summary and Received Headers.
This section shows general properties of email, along with all the servers that the email travels through before reaching the recipient mailbox.
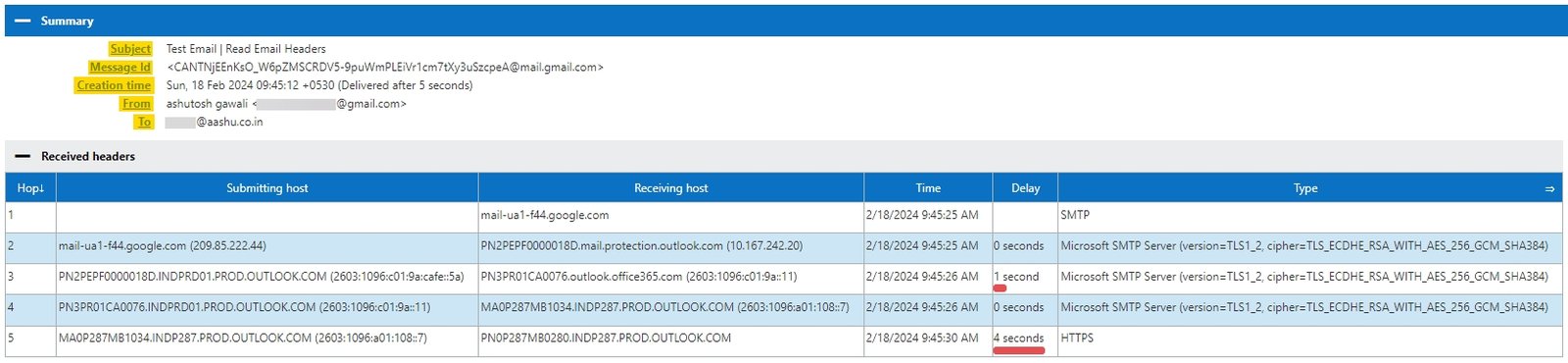
| From | The name and email address of the sender (this can be spoofed). |
| To | Shows the recipient of the email. |
| Subject | This is what the sender used as a topic of the email content. |
| Message Id | A unique identifier created and assigned by the sender email system to the email. |
| Creation time | The date and time when the email is sent. |
This section will also demonstrate if there is any delay between the sender server sending the email and the recipient server receiving it.
Forefront Antispam Report Header.
The values in this field shows how the EOP spam filters process the email.
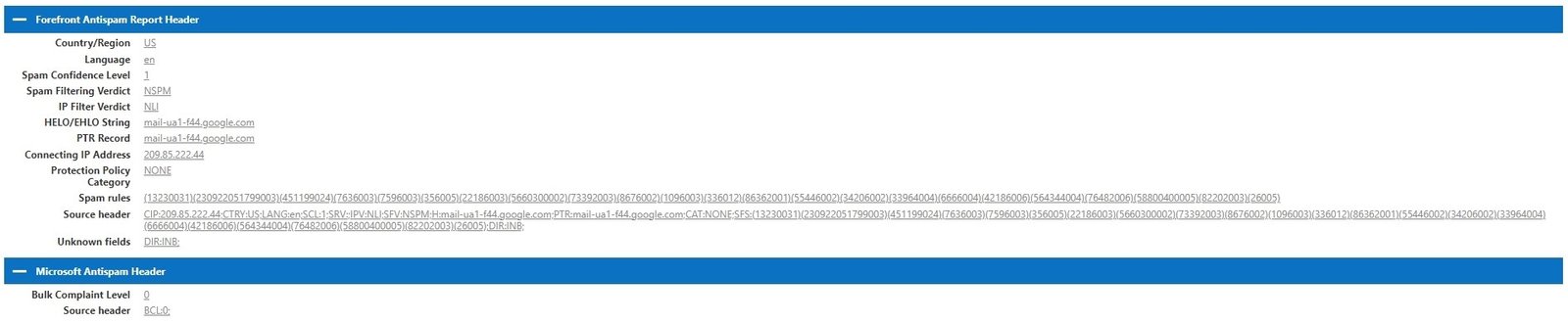
| Country/Region | The country/region is determined by the connecting IP address. |
| Language | The language used to write the email. |
| SCL (Spam Confidence Level) | SCL is the value assigned by the EOP to the email that was scanned for Spam. SCL: -1 | The email is Not Spam and allowed by either Admin or the user in your organization. (Safe Sender List created by the user, IP allow list, Transport Rule created by Admin) SCL: 0, 1 | The email is marked as Not Spam. SCL: 5, 6 | The email is marked as Spam. SCL: 7, 8, 9 | The email is marked as High Confidence Spam. |
| SFV (Spam Filtering Verdict) | It is the decision taken before the email gets to the content filter in EOP. SFV:NSPM | EOP marked the email as non spam and the message was sent to the intended recipients. SFV:SPM | The message was marked as spam by spam filtering. SFV:SKA | EOP allowed the email as the sender is present in the allowed senders list or allowed domains list in an anti-spam policy. SFV:SKB | The email was blocked as the sender is present in the blocked senders list or blocked domains list in an anti-spam policy. |
| IPV (IP Filter Verdict) | IPV:NLI | The connecting IP address is not listed in any DNSRBL. (List of bad IP addresses known to send spam or have bad reputation). IPV:CAL The email skipped spam filtering as the connecting IP address is in the IP Allow List. |
| HELO/EHLO String | The FQDN (fully qualified domain name) of the server which connected to EOP to deliver the email. |
| PTR (Reverse DNS) | The EOP will check the PTR record of the connecting server which sent the HELO/EHLO String. The PTR record maps the IP address to a hostname of the connecting server. |
| Connecting IP Address | The IP address of the server which connected to EOP to deliver the email. |
| Protection Policy Category | This value represents the policy in EOP which marked the email as Spam or Spoof. Example: Phishing Policy, Spoof, User impersonation, Bulk, Domain impersonation. If the email is marked as NonSpam then the protection Policy Category will show up as NONE. |
| Spam Rules | Use by EOP internally. |
| Source header | This will combined information (SCL, Language, PTR) about the connecting server. |
| DIR | This shows the directionality of the email to EOP. INB: Email is Inbound to EOP. OUT: Email is being sent OUT from EOP. INT: Email is Internal to EOP. |
| X-CustomSpam: [ASFOption] | This field shows if the email is processed for any Advanced Spam Filtering options setup in the Anti Spam policy. Example: Mark the email as Spam if the body of the email is Empty. |
| BCL (Bulk complaint level) | Bulk email is often one-time advertisements or marketing messages. BCL is the value assigned by the EOP to the email. BCL: 0 | The email is not from a bulk sender. BCL: 1, 2, 3 | The email is from a bulk sender that generates few complaints. BCL: 4, 5, 6, 7 | The email is from a bulk sender that generates a mixed number of complaints. BCL: 8, 9 | The message is from a bulk sender that generates a high number of complaints. |
Other Headers.
EOP and all the other servers stamped the below headers as the email passed through to reach the EOP.
| Authentication-Results | This section shows the result of the authentication methods (spf, dkim, dmarc) used by EOP. |
| Received-SPF | When SPF is checked by EOP, the results of SPF check will be stored in this section. |
| DKIM-Signature | If the sender server is using DKIM then the signature will be shown here. |
| MIME-Version | Multipurpose Internet Mail Extensions (MIME) is an extension of the Simple Mail Transport Protocol (SMTP) that allows sender to exchange different types of data files, such as audio, video, images, and applications, over email. If this header is present and the value of this header is 1.0 then the email is MIME formatted email. |
| Content-Type | It indicates the format of an email body. Example: Content-Type: text/plain; or Content-Type: multipart/alternative; Please check the article to understand Content-Type |
| Return-Path | If the message is rejected, it will be sent back to the email address listed here. |
| X-MS-Exchange-Organization-Network-Message-Id | A unique Message-Id created and used within Exchange Online. |
| X-MS-Exchange-Organization-MessageDirectionality | This field will confirm if the email is created (Originating) from the tenant or the email is received (Incoming) by the tenant. |
| X-MS-Exchange-Organization-AuthSource | Specifies the FQDN of the server that checked the authentication of the email on behalf of the tenant. |
| X-MS-Exchange-Organization-AuthAs | It shows from which sender the email is received from. Example: Internal, External, Anonymous, Partner. |
| X-Microsoft-Antispam-Mailbox-Delivery | This field shows to which folder of the recipients mailbox, the email was delivered to. jmr – Junk Mail Rule. dest:I – Destination folder is Inbox. dest:J – The email is moved to Junk Mail folder. dest:C – The email was delivered to a custom folder in recipient mailbox. OFR:CustomRules – Outlook rule changed the delivery of the email. OFR:SpamFilterAuthJ – The email was moved to junk by Spam filter or the sender is added in the recipients block senders list. |
Conclusion.
Analysing the email headers is not a daily job for the end user or an Administrator.
You can view the email headers using email client like Outlook and use different message header analyzer tools to analyse email headers.
Understanding the details of fields in email headers will come in handy when troubleshooting email deliverability issues, email delay problems, or confirming whether email authentication has passed for an email.