What is Microsoft Entra Connect Sync
Microsoft Entra Connect Sync is used to sync the users and other objects in on premises active directory to Microsoft Entra ID, In other words, Microsoft Entra connect Sync is integrates your on premises and online directories, making it easier to manage identities and other objects.
Table of contents
- Internal Components of Microsoft Entra Connect Sync (Architecture)
- Connected Directories (CD) & Connectors
- Connector Space (CS) & Metaverse (MV)
- Projection & Provision
- Synchronization Rules
- Import, Synchronization and Export Operations.
- Synopsis of how user syncs from local AD to Microsoft Entra ID.
- Conclusion.
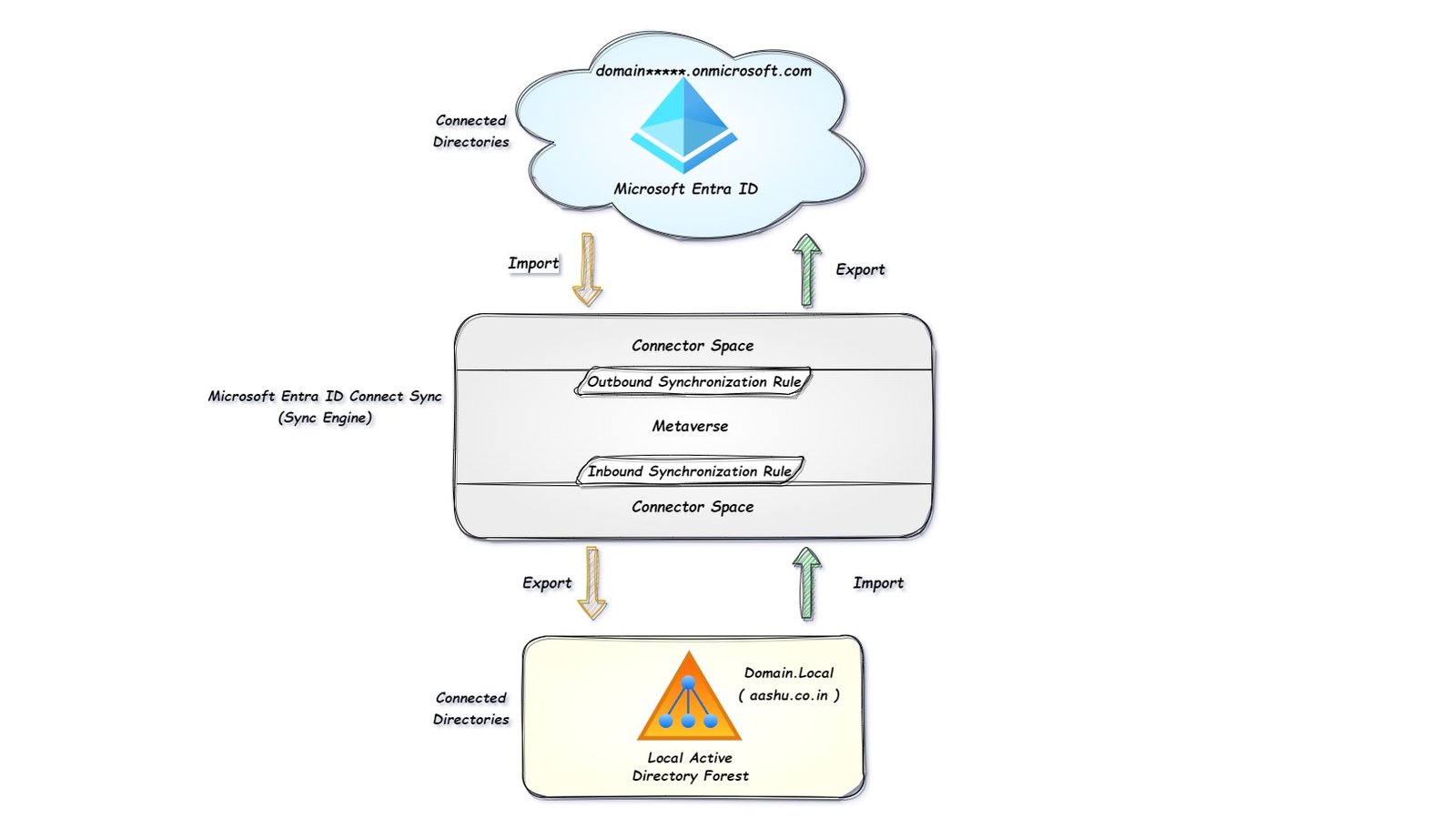
Internal Components of Microsoft Entra Connect Sync (Architecture)
Connected Directories (CD) & Connectors
The source of data objects (user, device, group, computer) is Connected Directories, which connect to the Azure AD Connect tool. The AD Connect tool can read data from Connected Directories or write data to Connected Directories.
In the diagram, we have two Connected Directories (CD) One is Local Active Directory in which we have verified Domain.Local (aashu.co.in) and another is Microsoft Entra ID where we have the tenant domain*.onmicrosoft.com
The connector is the logical entity that connects Microsoft Entra Connect tool with Connected directories (Local AD and Microsoft Entra ID).
In the below diagram, there are 2 connectors, one is Domain.Local (aashu.co.in), which is connecting the local AD to Microsoft Entra Connect tool, another is domain*.onmicrosoft.com – AAD which is connecting Microsoft Entra Connect tool with Microsoft Entra ID (cloud tenant)
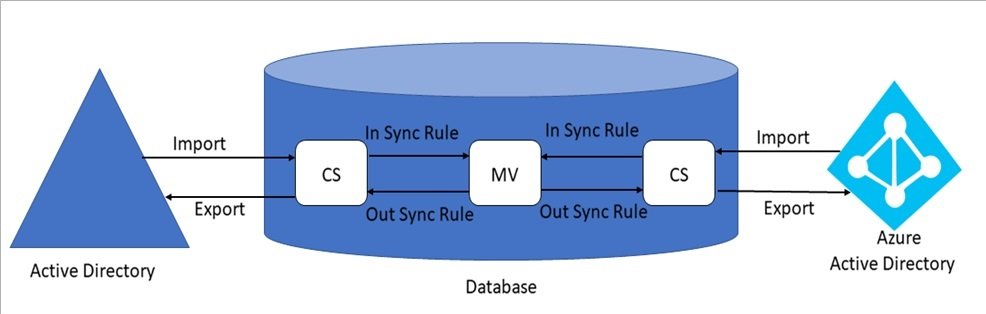
Connector Space (CS) & Metaverse (MV)
The connector space holds a representation of each object from a connected data source, and the attribute inclusion list for that data source. Each connector managed by the tool has its own connector space.
The connector space provides a way for the tool to compare what has changed in a connected data source so that it can correctly stage incoming changes or outgoing changes.
Metaverse is a virtual holding area which holds all the identity information from all the connected data source in a single unified view.
If we are syncing more than one local AD Forest, where there is more than one connected data source, each object from every forest gets represented once in the metaverse and synchronized to your target Microsoft Entra ID tenant.
Projection & Provision
The process in which an object in a connector space is allowed through a synchronization rule to move into the metaverse as a new object while maintaining a connection to its source anchor in connected data source is called a projection.
when a new object is created in a different connector space, is referred to as a provision.
Synchronization Rules
Synchronization rules are the default rules created when we install Microsoft Entra Connect Tool, synchronization rule will filter out the object which satisfy the criteria of the default rule or any custom rule created by the administrator.
Example: there is a default sync rule created that states not to synchronize any user whose [isCriticalSystemObject] attribute in attribute editor is TRUE, if we check in our local AD, all the administrators have [isCriticalSystemObject] TRUE, hence due to this rule, all the local administrator does not sync from Microsoft Entra Connect tool to Microsoft Entra ID.
Another Example of Synchronization Rule is for Group. [sAMAccountName] = “MSOL_AD_Sync_RichCoexistence”, that means if a group has sAMAccountName as “MSOL_AD_Sync_RichCoexistence” then the group will not sync to Microsoft Entra ID.
Inbound Sync rule will not let any local administrator account let into Metaverse (MV). The local administrator account will move to connector space but not into Metaverse, hence it will not be compared against any object in the cloud. Hence it will not move to Microsoft Entra ID.
The outbound synchronization rules are applied to every object present in the metaverse, based on the outbound sync rule condition the object will wither move to Microsoft Entra ID Connected Space or will not move or processed by Metaverse.
Import, Synchronization and Export Operations.
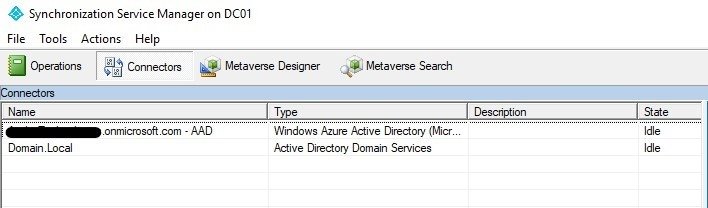
Once we open synchronization Service, on the main page we get 3 operations, using which an object will sync to from Local AD to Microsoft Entra ID.
Import Operation.
Import operation will collect object data from connected data sources (Local AD and Microsoft Entra ID) and send it to Connector Space (CS)
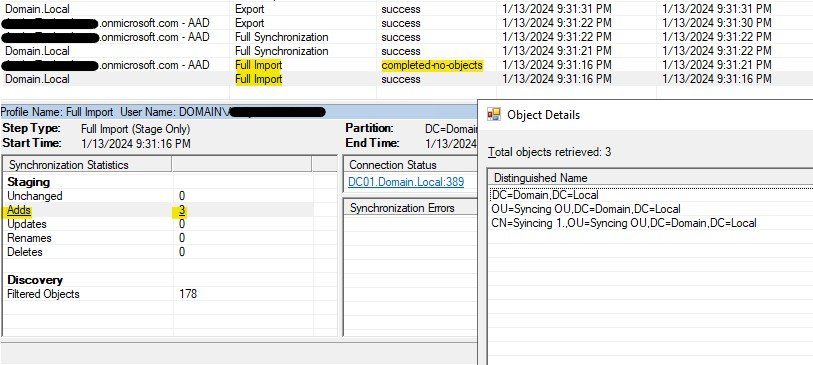
In the above image, if we select Domain.Local Import Operation, we get to know that 3 objects are added and moved to CS.
In the discovery section filtered object is showing as 178, this is because I am only syncing one OU with few objects. There are other 178 objects in the local AD, which are skipped due to OU level filtering in Microsoft Entra Connect Sync.
There is another Import connector for Domain*.onmicrosoft.com – AAD this means Microsoft Entra Connect Sync is trying to import objects from Microsoft Entra ID into Connector Space (CS), as there are no objects currently in Azure AD to sync to Connector Space, it is showing as (Completed-no-objects).
Delta Import means only changes in the object attributes (properties) will be imported to CS, full import means all the objected will be imported to CS, if there is any object which has no changes made but the object is present in syncing OU, that object will also be imported to CS.
Synchronization Operation.
The next Operation performed by Microsoft Entra Connect is Synchronization.
When the object is moved from Connector Space into Metaverse then it is called Inbound Synchronization.
When the object is moved from Metaverse to Connector Space then it is called as Outbound Synchronization.
Before Inbound and outbound synchronization, Inbound and outbound synchronization Rules will apply, the rules will check the conditions and will not let the objects move to Connector Space and Metaverse, respectively.
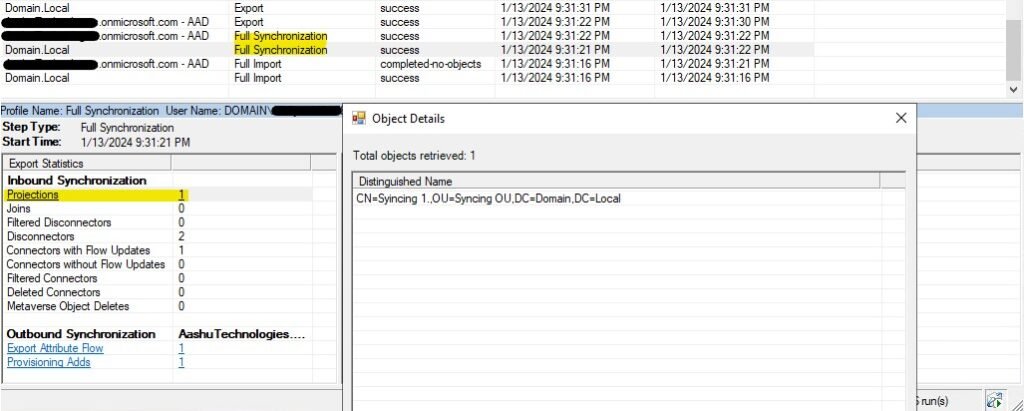
In the inbound Synchronization, we can see that there is 1 object (Projections) which is moved from CS (Local AD) to MV.
In the outbound synchronization, we can see that there is 1 object (Provisioning Adds) which is moved from MV to CS (Microsoft Entra ID).
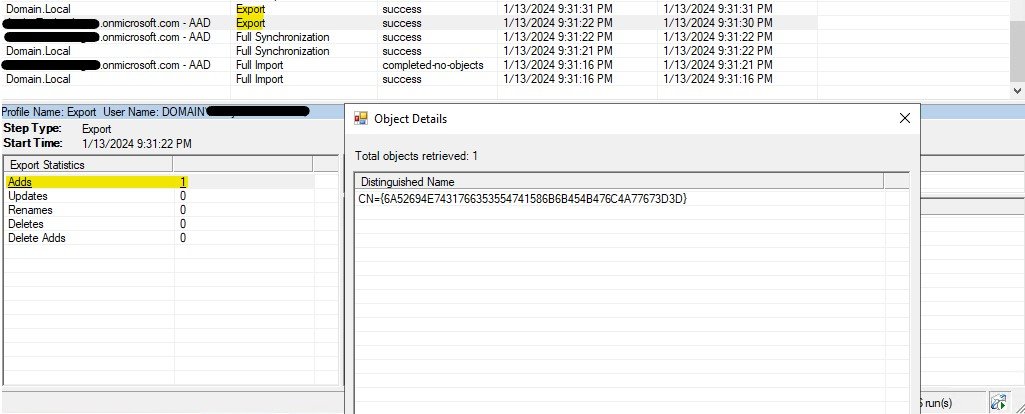
Export Operation.
Export operation will allow the objects to export to Connected Data sources.
For export operation in domain*.onmicrosoft.com – AAD Domain gave us 1 Microsoft Entra ID result, this means 1 object is added to Microsoft Entra ID from On premises AD.
For domain.local there will be no results, as nothing is imported into local AD.
Synopsis of how user syncs from local AD to Microsoft Entra ID.
Now, let’s check all the operations together when a new user is added to Local AD and how the user syncs to Microsoft Entra ID
- The user object in local AD user*@aashu.co.in will be moved to Connector Space (CS) using Domain.Local connector (Import operation from Local AD).
- The Microsoft Entra Connect Tool will check for any object from Microsoft Entra ID and that will be moved to Connector Space (CS) for Azure AD (Import operation from Microsoft Entra ID).
- After moving to CS, inbound synchronization rule will apply, if there is no rule to block the object, then the object user*@aashu.co.in will move to Metaverse. (Projection) (Synchronization operation from Local AD) In Metaverse the object user*@aashu.co.in will be compared with the Connector Space object of Microsoft Entra ID, there will be no object with the source anchor of user*@aashu.co.in in Microsoft Entra ID.
- Outbound synchronization rule will apply, and the object will be moved to Connector Space (CS) of Microsoft Entra ID (Synchronization operation for Microsoft Entra ID).
- In the Export operation the object user*@aashu.co.in will be exported to Azure AD (Export operation for Microsoft Entra ID), we do not have any object to be exported to local AD hence the Export cycle will be blank (Export operation for local AD).
Conclusion.
Microsoft Entra Connect tool provides many options to synchronize identities, manage authentication, it is customizable as per organizations hybrid environment by providing a unified identity solution.
With Microsoft Entra Connect, organizations can provide a seamless login experience to the users, which reduce the need for multiple usernames and passwords (Single Sign On).