In the article “A Deep Dive into Microsoft Entra Connect Sync” we have understood how the Microsoft Entra Connect works, now lets understand the options and the settings at the time of installation.
Table of contents
- Express Installation Option.
- Custom Installation option.
- Conclusion.
Install Microsoft Entra Connect on a domain-joined Windows Server 2016 or later.
Please check the Microsoft article for all the Prerequisites for installing Microsoft Entra Connect
While installation, you get 2 options
Express Installation Option.
In Express installation option, Microsoft Entra Connect Sync setup will proceed with default configuration.
- You will be prompt to Connect to Microsoft Entra ID, as a global administrator.
- After completing the above steps, the system will prompt you to log in to the local Active Directory domain as an Enterprise administrator.
- Then the setup will ask you to select the domains to sync to Microsoft Entra ID.
- After the above step, You may choose to start the synchronization of objects by selecting the check mark option.
In Express Installation option, all the OU, users and groups will sync to AD, if we do not want that then we have to go with custom installation option.
Custom Installation option.
When we select custom installation option, we get the below options on the setup page.
Install required components.
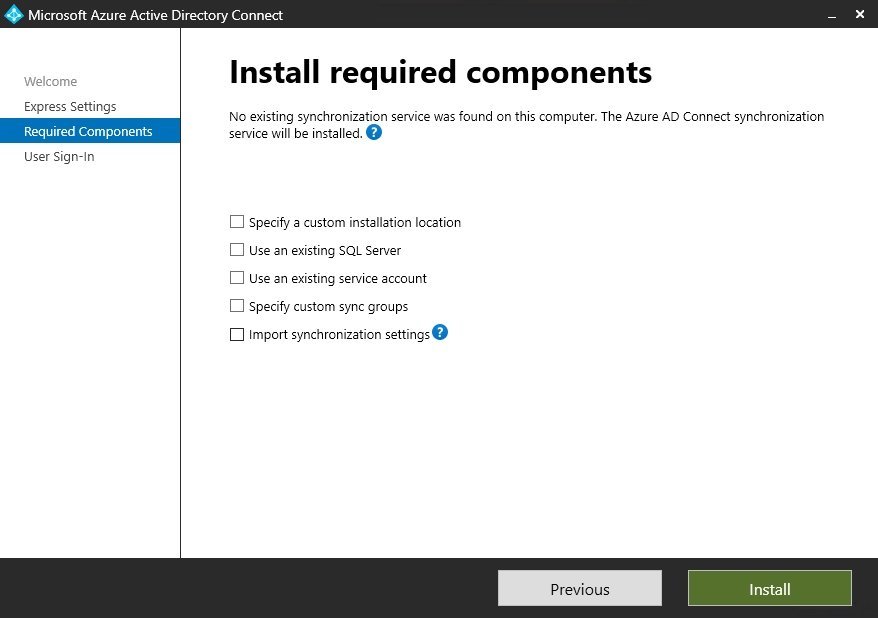
Specify a custom installation location.
With this option we can chose to install AD Connect tool in a different directory.
Use an existing SQL server.
when you installed Microsoft Entra Connect using default configuration, a new database named ADSync was created, this is because Microsoft Entra Connect requires a SQL Server database to store data.
using this selection, you have the option to install Microsoft Entra Connect by pointing it to an existing ADSync database on SQL server.
If your organization has more than 100,000 objects it is recommended to use full version of SQL server.
Use an existing service account.
There are many organizations which do not permit to use an enterprise administrator account while logging into any tool due to security reasons. If we select this option, we get to use either managed service account or domain service account in AD Connect tool
Managed service account is those account which are system managed and its password changes after a specific interval of time, while domain managed accounts are centrally managed.
Specify custom sync groups.
By default, the installation of the AD Connect tool creates four groups.
- ADSyncAdmins: the members of this group have full access permission to do anything in sync service manager.
- ADSyncBrowse: members have permission to gather information about password reset and other error information.
- ADSyncOperators: the members can run sync statistics and check sync history.
- ADSyncPasswordSet: member can reset password and perform other tasks related to password management.
If we select the option to specify the custom sync group, we can select other groups instead of default groups.
Import synchronization settings.
Use this option when upgrading the server or configuring a new server, and you require the exact settings from the previous server where Microsoft Entra Connect was installed.
We simply use a JSON file of configuration settings of previous server and import the configuration in new server
User Sign-In
After completing the installation of the required components, proceed to select the password synchronization and single sign-on options in the setup.
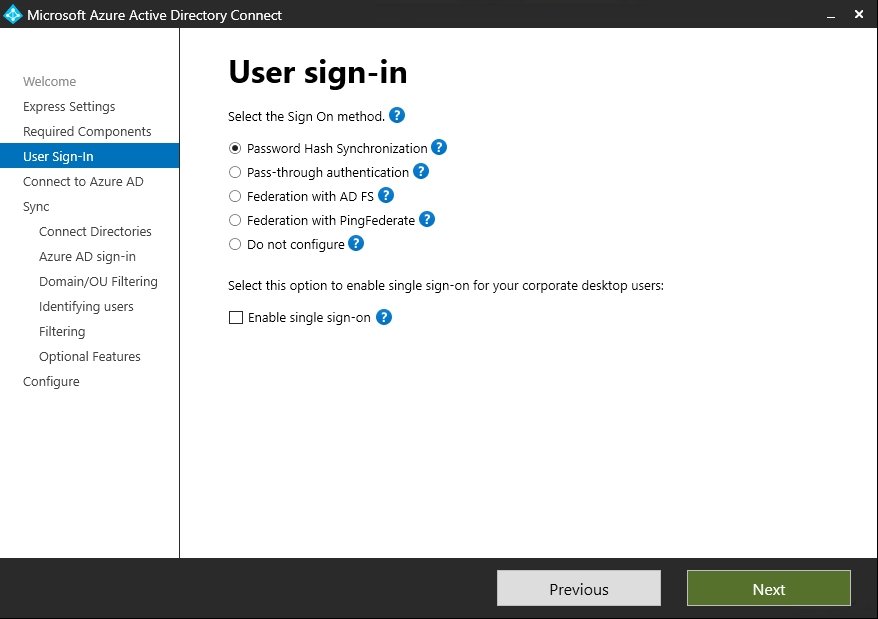
Password hash synchronization.
If we select this option, then a hash of user password is synchronized to Microsoft Entra ID.
All the password for synced users can be managed locally (from local active directory), users can reset their own password from Microsoft 365 but they need Microsoft Entra ID P1 or P2 license, and of course password right back should be enabled.
Pass through authentication (PTA).
If you do not want to use the password hash synchronization and your organization does not have any authentication mechanism on place like ADFS or PingFederate, then we can use PTA.
Let’s say a Synced user tries to login into https://portal.office.com and the PTA option is enabled for the tenant, them the password the synced user inputs at the time of login will be sent to the Local Active Directory using a PTA agent (installed in your local network).
The job of this PTA agent is to monitor the authentication request for synced user and confirm if the password entered is correct or incorrect, in addition to declaring an argument if the user can login using that password or not.
PTA agent will never investigate your local active directory for user’s password. PTA agent will just give the username and password which it receives from office 365 to the local Active directory, local AD will validate the username password and proved an argument (password expire, invalid username and password, login success) PTA agent will then forward the argument to office 365.
Federation with ADFS.
After selecting this option, the system redirects all authentication requests of synced users to the local ADFS for authentication.
Federate with PingFederate.
PingFederate is another identity authentication provider. It works same as ADFS.
Do not configure.
Selecting this option allows setting all the passwords for synced users from Microsoft Entra ID.
In the local AD, we can set different passwords for users and for the users synced to the tenant.
Enable Single sign on.
This option is only available with both password hash sync and pass-through authentication.
Single sign-on automatically signs users into both on-premises and cloud-based applications, when they are on their corporate devices connected to your corporate network.
Connect to Microsoft Entra ID.
On this page, log in using Global admin credentials of the tenant you want to sync the users to. It is always recommended to use the GA with onmicrosoft.com domain in this option.
Sync Options.
This section contains various settings that determine which users should be synced to the cloud, which property should be used for the synced user to log in to the tenant, and various other options.
Connect Directories.
In this section, you will need to log in to your Active Directory Domain Services (AD DS).
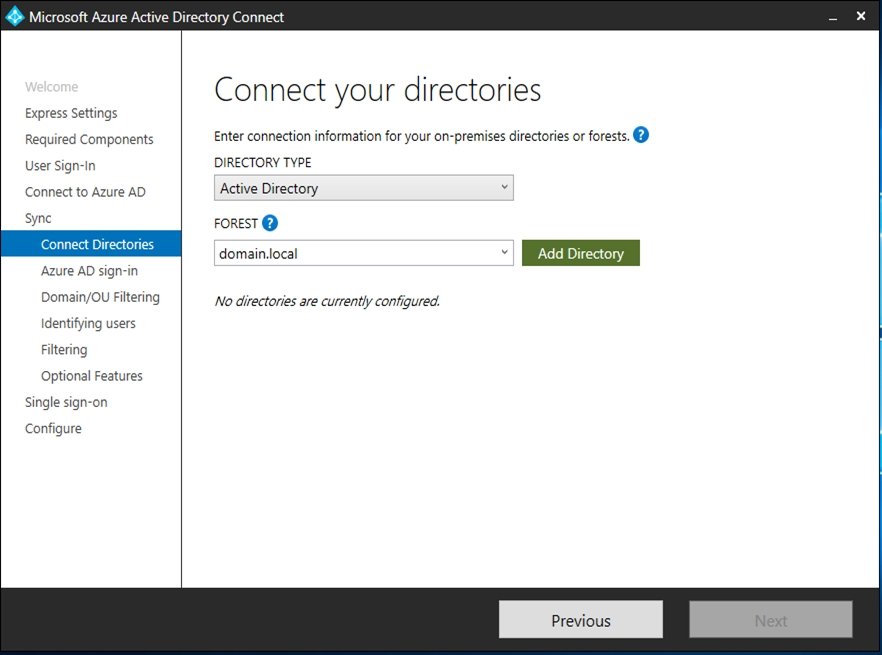
Once you select add directory option the following pop up will appear.
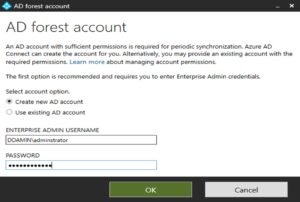
- Create new AD account: Create the AD DS account that this tool will use to connect to the local Active Directory forest during directory synchronization.
- Use existing AD account: You can also provide an existing AD DS account that this tool will use to connect to the Active Directory forest during directory synchronization.
Microsoft Entra sign-in configuration.
On this page, the setup will show how many domains the local AD has and how many domains Microsoft 365 has, If you have Domain*.com which is present in Active Directory domains and trust but not verified in Microsoft 365, then the domain will show up as unverified.
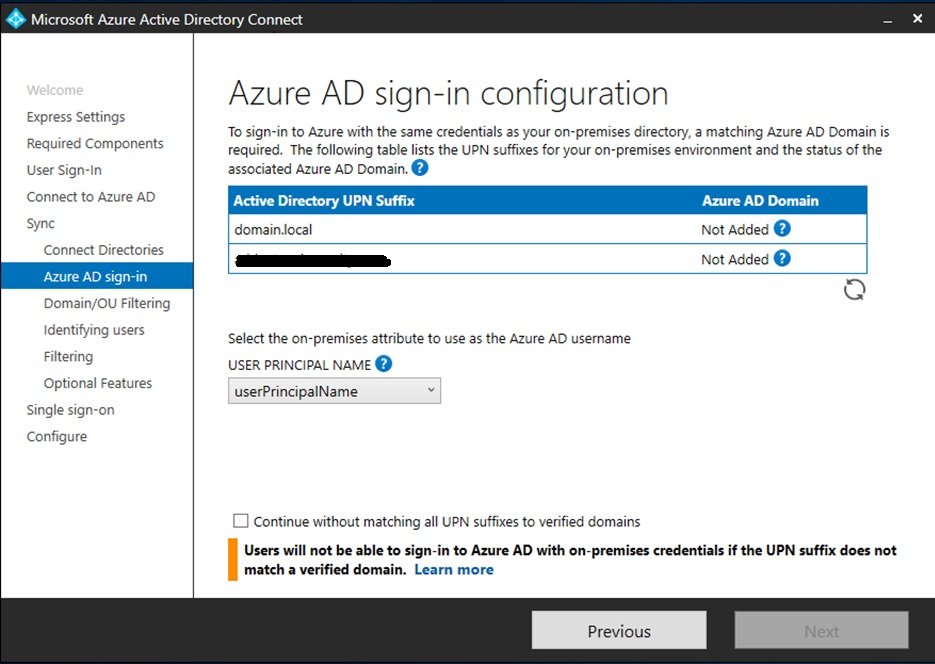
There is a statement which says “select the on-premises attribute to use as the Azure AD username”
userPrincipalName
This means that Microsoft 365 will use the on premises UPN to login into Microsoft 365, we have an AD user Ashutosh whose UPN is set to ashutosh@aashu.co.in then Microsoft 365 synced user Ashutosh can use ashutosh@aashu.co.in into https://portal.office.com (login into Microsoft 365)
Domain and OU Filtering.
Once we get to Domain and OU Filtering setup page, we get to select the domains or OU which we want to sync to Microsoft 365, if we select a specific OU then only the users in the OU are going to sync to Microsoft 365.
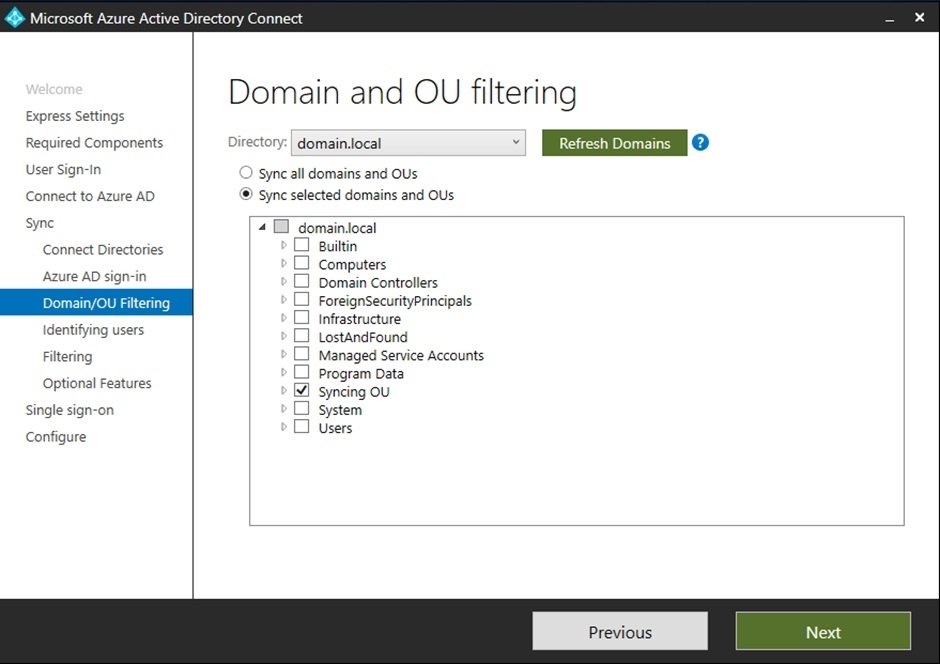
We also have an option to sync all domains and OU.
The users attribute which has attribute “is system critical object” set to True will not synchronize to the tenant directory, all the local enterprise admin account will have the attribute “is system critical object” set to True.
You can perform other custom synchronizations by creating new sync rules.
Sync rules apply before syncing the objects to the tenant directory. We can create custom sync rules like, do not sync users with attribute “custom attribute 1″ if it has value set to “xyz”, now in this case the users with whose custom attribute 1 is xyz will not sync to the tenant directory.
Uniquely Identifying your users.
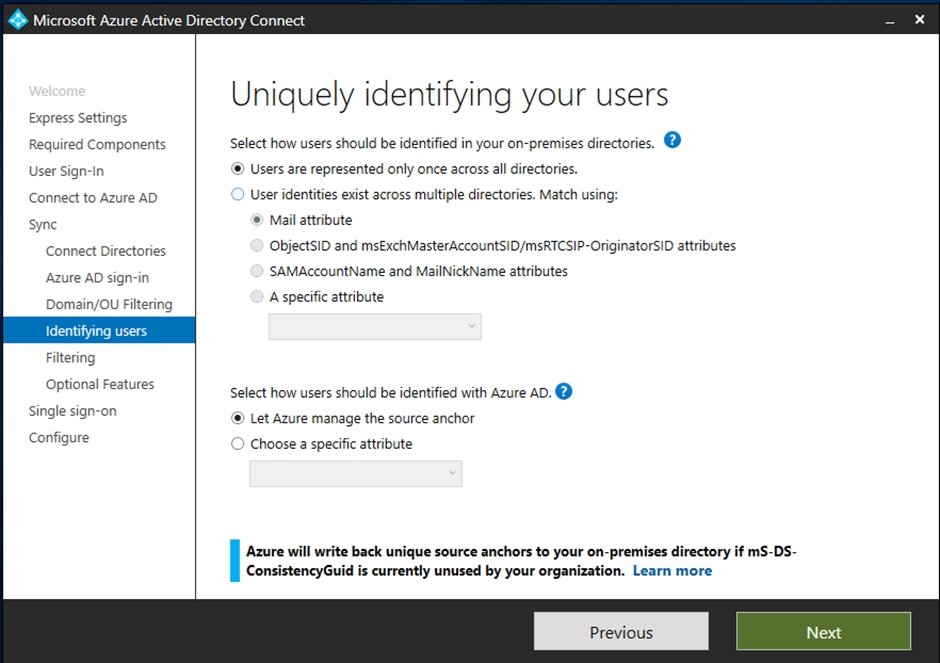
In uniquely identify the user’s section setup page, we get the below options,
Users are represented once across all directories.
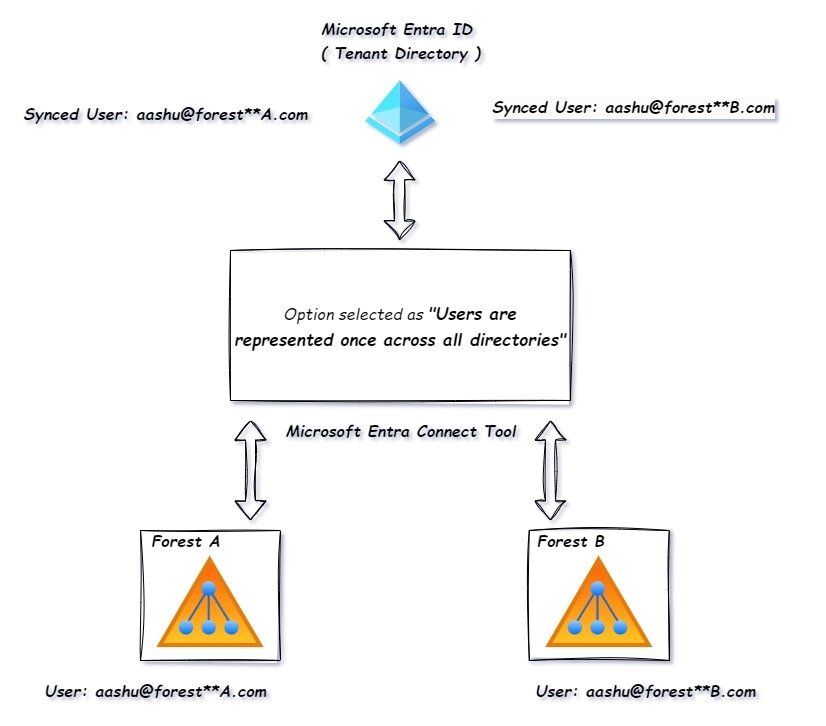
Use this option to ensure that the object to be synchronized is represented once across all the forests in a multiple forest scenario.
Example. If we have 2 forest in Local Active Directory, and we are syncing both the forest using Microsoft Entra Connect tool. We have the user aashu in forest A with UPN aashu@forest**A.com and we have another user in different forest with UPN aashu@forest**B.com and both the forest are syncing via same Microsoft Entra Connect tool then in Microsoft 365 there will be 2 users aashu@forest**A.com and aashu@forest**B.com
Microsoft Entra Connect tool will portray the 2 accounts to be different as they are in 2 different forest.
User identities exist across multiple Directories (Forest) Match using.
Mail Attribute
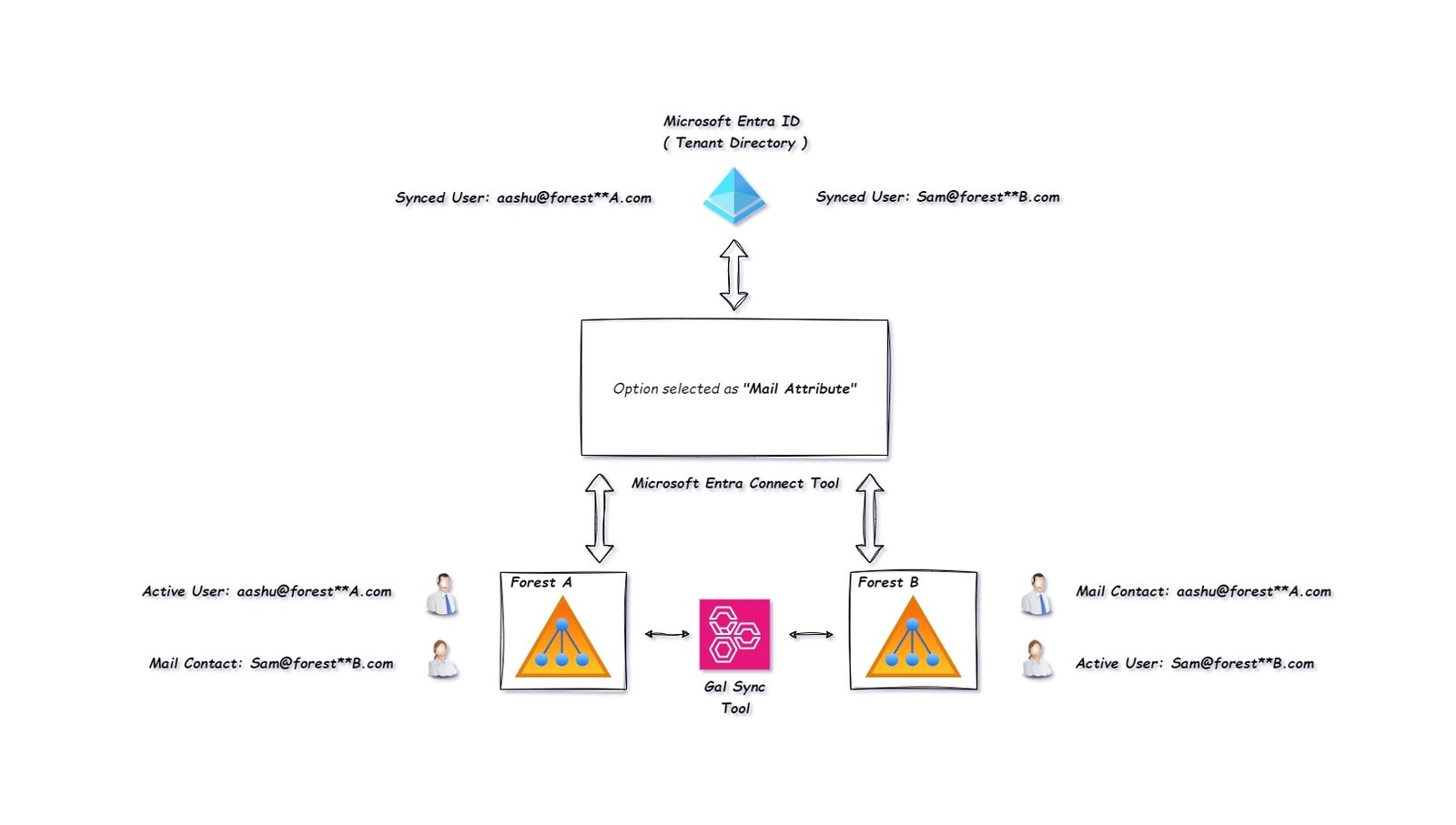
Now imagine you have 2 different forest in on premises AD but both forests are joined using GALSYNC tool, which is a tool used to sync the GAL in Forest A to Forest B.
All the active users in forest A will have a mail contact in Forest B, and vice versa. Microsoft Entra Connect tool is syncing 2 Forest to Microsoft 365.
Forest A = aashu@forestA.com (Active user) and Sam@forestB.com (mail contact)
Forest B = Sam@forestB.com (Active user) and aashu@forestA.com (mail contact)
Instead of 4 users Microsoft Entra Connect will sync 2 users as we are letting the tool know that there are multiple forest syncing to Microsoft 365 using this tool and the tool should use mail attribute to sync users to cloud properly.
If the tool finds multiple entities using same UPN (one active user and another mail contact) then the tool should only sync active user.
Microsoft Entra Connect will merge mail contact and active user for the same UPN which are in different forest and will only sync the Active user to Microsoft 365.
ObjectSID and msExchangeMasterAccountSID/ msRTCSIP-OriginatorSID attributes.
This option is used when we have account forest and resource forest scenario, typically we have enabled user in account forest with disabled user in resource forest. The tool will join the object which is enabled in account forest with the object which is disabled in resource forest.
SAMAccountName and MailNickName.
Use this setting when you want to merge the two attributes in different forests.
Specific Attribute.
If we use a specific attribute that means we only want to sync the users who has the specific attribute field set, if the specific attribute field is blank then the user is will not sync to Microsoft 365
Source Anchor.
Another option to select is “Select how users should be identified with Azure AD.” By using source anchor.
Now the question is what is source anchor? source anchor is the glue that binds the on-premises user with the user which is synchronized tothe tenant (to Microsoft 365 Entra ID).
Source anchor is immutable in the lifetime of the object, that means source anchor cannot be changed once the user or object is synced to Microsoft 365 from on-premises active directory.
Newer version of Microsoft Entra Connect uses ms-DS-ConsistencyGuid as sourceAnchor attribute. earlier versions uses ObjectGUID was used as source anchor.
ObjectGUID is a value that is system generated when any object is created, but ObjectGUID is changed when we move the object from one forest to another forest, even if the object is deleted and recreated the ObjectGUID value is changed.
This is not desirable when ObjectGUID is used as source anchor, as if we move an object from one forest to another, the ObjectGUID for the object will change and another object will be created.
If any object is deleted and created again the ObjectGUID will change and again another object will be created.
All this can be solved if ms-DS-ConsistencyGuid is used as source anchor, if for a user ms-DS-ConsistencyGuid attribute is not populated, then Microsoft Entra Connect will write the ObjectGUID value to ms-DS-ConsistencyGuid attribute in on-premises Active Directory, then the user will be synchronized to Microsoft 365.
Filter Users and Devices.
This option is used if you wat to synchronize a group of pilot users, devices, computers or contacts to office 365, we can add more users in the group later.
This is only supported for pilot deployment of Microsoft Entra Connect Tool.
Optional Features.
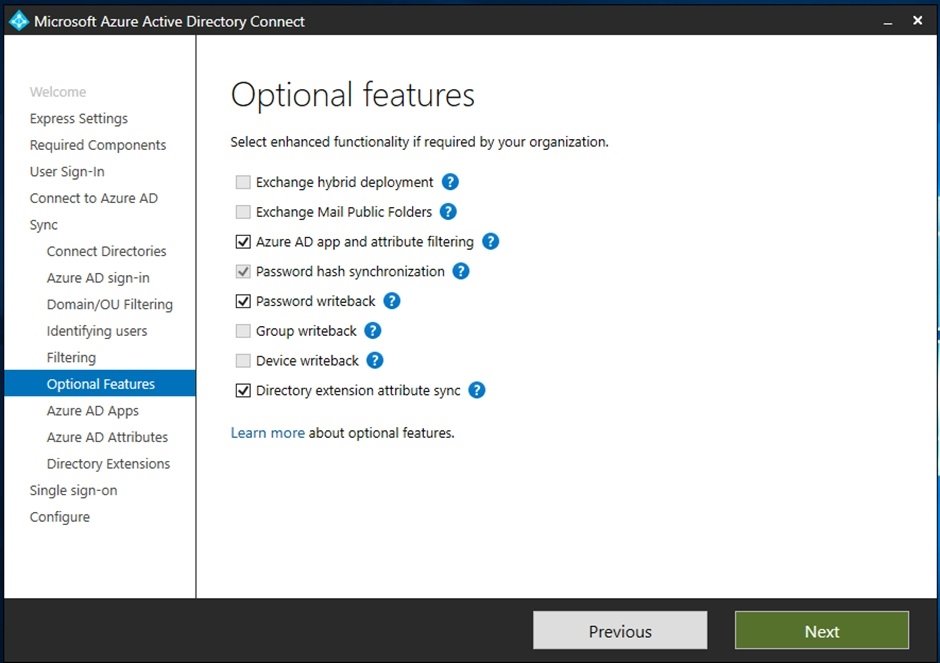
Exchange hybrid deployment.
If you enable this option then few attributes will be written back from Microsoft Entra ID to on-premises Active Directory.
Please check the list of attributes that can be written back in the Microsoft article Exchange hybrid writeback
Exchange mail public folders.
With the help of this option, we can synchronize mail enabled public folders from Exchange on-Premises to Microsoft 365.
Microsoft Entra ID app and attribute filtering.
If we select this option, then we get to choose which attributes of the selected applications will sync to Microsoft Entra ID.
Example: If an organization does not want all the custom attributes to sync to Exchange online via this tool then they can remove the Exchange online application from the Microsoft Entra ID Apps, the drawback would be, all the attributes that Exchange online application use will not sync to Microsoft Entra ID.
Microsoft Entra Attributes.
This section will provide us option to further remove any attributes which we do not want to sync to Microsoft Entra ID.
Please check the list of attributes that by default sync to Cloud in the Microsoft article Attributes to synchronize
Directory Extension attribute sync.
We can extent the schema of Microsoft Entra ID by adding the attributes in this section, suppose my organization has created and published a custom application in Microsoft Entra ID application gallery,
If the custom application needs the attribute admincount and admindescription to work in Microsoft Entra ID, then I will select admincount and admindescription in this section and the attributes will be added to Microsoft Entra ID schema in Cloud.
Password Writeback.
This option is used when we want the company users to change the password from cloud and it will write back to on premises authentication provider.
For Password Writeback to work, we need to have the user assigned with Microsoft Entra ID P1 license, and Self Service Password Reset (SSPR) should be enabled for the user from Microsoft Entra ID Portal.
Group Writeback.
After enabling this option our Microsoft 365 groups (Office 365 groups) will be written back to on premises Active Directory, this will only work if we have Hybrid installed and working between Microsoft 365 (Exchange Online) and On Premises Exchange server.
Device Writeback.
If your organization wants to use the option of On-Premises Conditional access and Windows Hello for business then Device write back is the prerequisite for using the 2 features, after enabling device writeback, this tool will synchronize all the devices registered in Microsoft Entra to On-Premises.
Enable Single Sign ON
We must enter the credential of Enterprises administrator in this process, after this process we have to add the url “https://autologon.microsoftazuread-sso.com” and “https://aadg.windows.net.nsatc.net” in all or selected users’ Intranet zone settings by using Group Policy in Active Directory. Then SSO will work for all browsers.
Final Configuration.
After selecting Single Sign on option, we will get to the final configuration page, please notice that there are 2 options.
| Option 1: Start the synchronization process when the configuration completes | If we check mark this option, then Microsoft Entra connect will synchronize all the objects to Microsoft Entra ID after the configuration completes. |
| Option 2: Enable Staging mode: | If we select this option, then the tool will not synchronize any object to Microsoft Entra ID, it will become passive as there will be another active Microsoft Entra Connect server syncing the Objects to Microsoft Entra ID. If the active server goes down, then another administrator will have to manually make the switchover for this server from Passive to Microsoft Entra Connect server. |
Conclusion.
Microsoft Entra Connect tool provides many options to synchronize identities, manage authentication, it is customizable as per organizations hybrid environment by providing a unified identity solution.
With Microsoft Entra Connect, organizations can provide a seamless login experience to the users, which reduce the need for multiple usernames and passwords (Single Sign On).