Multifunction devices (MFD) refers to an application (third party or inhouse) or a device (printer, scanner) that can send the email to internal or external users using Microsoft 365 infrastructure.
There are various ways that multifunction devices uses to send the email to the recipient. Different options has its own benefits and limitations. Before exploring how each option works and connects to Microsoft 365, let’s first understand a few key concepts.
Table of contents
- Smart Host (Microsoft 365 Endpoints).
- TLS (Connection Encryption).
- Basic Auth vs. Modern Auth.
- Messaging Protocols.
- Deprecation of Basic Authentication in Exchange Online.
- Methods of connecting MFD to Microsoft 365.
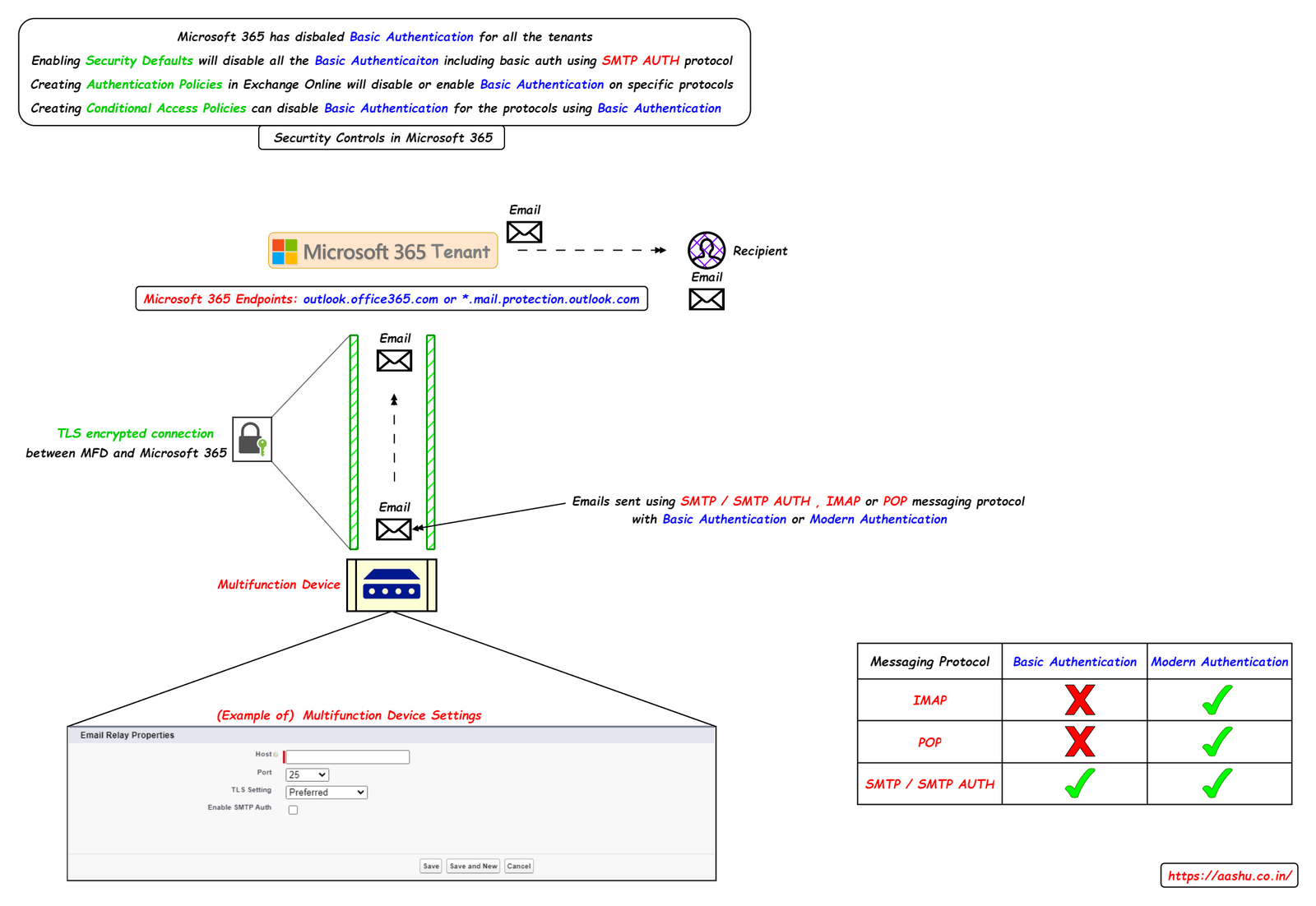
Smart Host (Microsoft 365 Endpoints).
Microsoft 365 endpoints are the servers that an MFD (multifunction device) connects to when it needs to send an email or authenticate user credentials. Example: outlook.office365.com or *.mail.protection.outlook.com or login.microsoftonline.com
All Multifunction devices or email sending application have an option to setup the server / smart host. This is where the application sends the email to.
Different services in Microsoft 365 uses different endpoints, to get the list of all the endpoints used by different services, check Microsoft 365 URLs and IP address ranges.
TLS (Connection Encryption).
Transport Layer Security (TLS) is a connection encryption protocol which is used to encrypt the connection between the Multifunction Device and the smart host (Microsoft 365 endpoint). Once encrypted, all data between the MFD and smart host is securely transmitted through the encrypted channel. TLS doesn’t encrypt the message that is sent, it just encrypts the connection between MFD and smart host.
Basic Auth vs. Modern Auth.
Basic Authentication is when the username and password are stored in the Multifunction devices and it is sent with every request (emails that are being sent using MFD) to Microsoft 365. Microsoft 365 checks the username and password, if it is correct then the email will be delivered to the recipient, or else you will get an error 535 5.7.3 Authentication unsuccessful or 5.7.57 Client not authenticated to send mail.
The problem with storing and sending the username and password with Multifunction device is when the username and password is compromised, then whoever gets the username and password can use it to login to Microsoft 365 and perform numerous actions from that logged in user.
In Modern Authentication, instead of username and password, the application uses app passwords, certificates or tokens when sending email using Microsoft 365. Weather the application uses basic auth (username / password) or modern auth (app passwords, certificates or tokens) to send email depends on what auth method the application is developed to be used. example, if the application was developed many years ago, it probably uses only basic auth (username / password) to send emails. If the application is developed recently or it is one of new saas applications then it would support the modern auth options (app passwords, certificates or tokens).
Messaging Protocols.
Messaging protocols are the protocols used by the Multifunction device to process the emails and send or read emails using Microsoft 365 endpoint. Example of messaging protocols are IMAP, POP and SMTP / SMTP AUTH. SMTP is the protocol used to send and receive emails, SMTP AUTH is an extension to SMTP protocol where the SMTP client (Multi Function Device) sends an authentication mechanism (basic auth or modern auth) to the Microsoft 365 endpoint.
Application developers develop the application to use any messaging protocol with either basic auth or modern auth (in some scenarios both).
Example: Microsoft 365 will not authenticate POP and IMAP if they use basic authentication, but Microsoft 365 will authenticate SMTP / SMTP AUTH protocol using basic authentication (In September 2025 Microsoft 365 will permanently remove support for Basic authentication with SMTP AUTH)
Microsoft 365 can authenticate IMAP. POP and SMTP / SMTP AUTH if they use modern authentication. There are few steps which needs to be performed on Microsoft 365, if the Multifunction device is using modern authentication, the steps are mentioned in the article Authenticate an IMAP, POP or SMTP connection using OAuth.
| Messaging Protocol | Basic Authentication | Modern Authentication |
| IMAP (Port: 993) | No | Yes (Authenticate an IMAP, POP or SMTP connection using OAuth.) |
| POP (Port: 995) | No | Yes (Authenticate an IMAP, POP or SMTP connection using OAuth.) |
| SMTP / SMTP AUTH (Port 587 / 25) | Yes (only till September 2025) You can Enable or disable SMTP AUTH in Exchange Online. | Yes (Authenticate an IMAP, POP or SMTP connection using OAuth.) |
Deprecation of Basic Authentication in Exchange Online.
Microsoft 365 has disabled basic authentication for all the tenant. (current exception SMTP AUTH protocol till September 2025). For an administrator there are multiple ways to block the basic authentication in Microsoft 365.
- Security Defaults (tenant wide setting): Security defaults are the pre configured settings in Microsoft 365 that will disable all the basic authentication methods on the tenant, forces all the users and administrators to setup multifactor authentication (MFA).
- Authentication Policies (per user setting): Authentication policies are the rules created in Exchange Online to disable or enable the basic authentication based on protocol used. Authentication Policies can be created using PowerShell command New-AuthenticationPolicy.
- The command New-AuthenticationPolicy -Name “Test Group” -AllowBasicAuthImap will create a new Authentication Policy on the users in the group “Test Group”, hence the basic auth for IMAP protocol will be enabled
- Conditional Access Policies: Conditional Access Policies are set of rules created on Microsoft Entra ID side, conditional access policies triggers after the user enters the username and password. It will apply specifically to clients that uses basic authentication and blocks them to access the resources. To know more about conditional access policies read the article What is Conditional Access?
Methods of connecting MFD to Microsoft 365.
We can connect multifunction devices to Microsoft 365 using basic or modern auth with protocols like SMTP, IMAP, and POP. It depends on how the MFD is designed to connect to Microsoft 365.
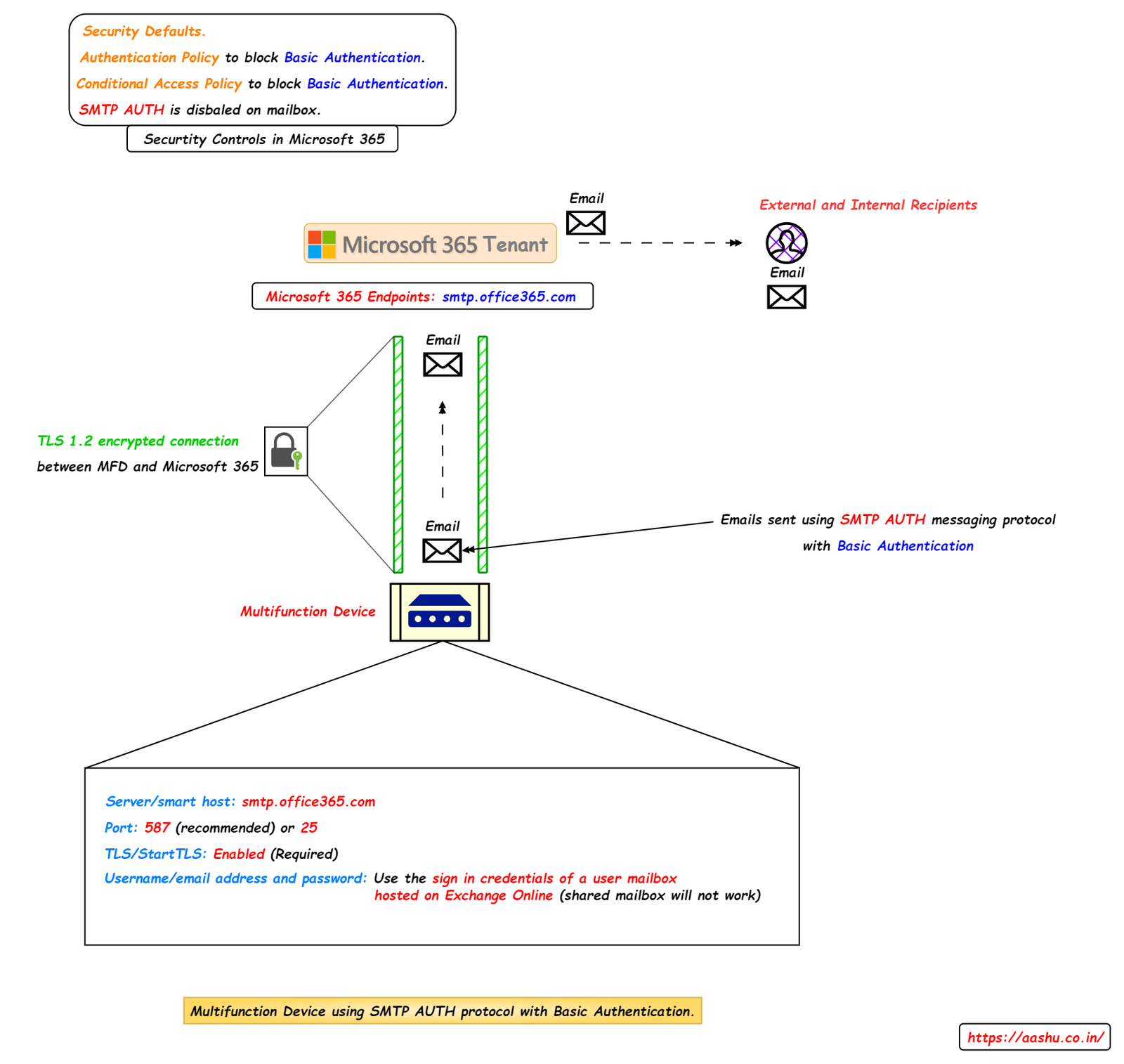
Method 1: SMTP AUTH client submission (Basic Auth).
If an organization is using legacy application or Multifunction device that uses basic authentication with SMTP AUTH protocol, then the organization can use the method called SMTP AUTH client submission to connect the MFD to Microsoft 365 and send emails. This method will only be available till September 2025 as Microsoft 365 will disable the support for SMTP AUTH protocol on Basic Authentication.
Below settings should be configured in MFD to use SMTP AUTH method.
- Server/smart host: smtp.office365.com
- Port: 587 (recommended) or 25
- TLS/StartTLS: Enabled (Required)
- Username/email address and password: Use the sign in credentials of a user mailbox hosted on Exchange Online. (shared mailbox will not work).
SMTP AUTH will fail if.
- Organization has enabled Security Defaults (which disables Basic Authentication).
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, user is locked by your organization’s security defaults policy. Contact your administrator.
- Organization has configured Authentication Policies to disable Basic Authentication based on messaging protocol.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, basic authentication is disabled.
- Organization is using Conditional Access Policy to block the Basic Authentication.
- Error: The SMTP server requires a secure connection or the client was not authenticated. the server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, the request did not meet the criteria to be authenticated successfully. Contact your administrator.
- Organization has disabled the SMTP AUTH protocol on tenant level or mailbox level. check the article Enable or disable authenticated client SMTP submission (SMTP AUTH) in Exchange Online.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, SmtpClientAuthentication is disabled for the Mailbox.
- The Multifunction device is not using TLS 1.2 to encrypt the connection between MFD and Microsoft 365.
- Error: The server response was: 5.7.3 STARTTLS is required to send mail.
- If your ISP or organization network firewall is blocking port 25 or port 587, this will not let the MFD to connect to Microsoft 365.
- Error: Unable to connect to the remote server.
- The email address is blocked for sending spam emails and is showing up in Restricted entities page in Microsoft Security portal.
- You might not get any error while you try to send any email using MFD and when the email address is blocked in the restricted entities page (it depends on the application if we get an error or not).
- When the email account used in MFD (while authenticating) has insufficient send as permission on the email sending mailbox (which is used in from address in the MFD).
- Example: While authenticating we provided the upn as Printer@aashu.co.in but in the from address we provided the email address as Scanner@aashu.co.in when we try to send email using the MFD and if the email address Printer@aashu.co.in does not have send as permission on Scanner@aashu.co.in then we will get the error: The server response was: 5.2.252 SendAsDenied; Printer@aashu.co.in not allowed to send as Scanner@aashu.co.in
- If your MFD does not have any option to input the credentials (password) then the MFD does not support SMTP AUTH Client Submission method to send the email.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, Client was not authenticated to send anonymous mail during MAIL FROM.
- The password is incorrect then the MFD might show the below error.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, the user credentials were incorrect.
Key points to remember about SMTP AUTH.
- The emails sent from Multifunction device using SMTP AUTH Client Submission are not subjected to email filtering in EOP (email bypass most of the spam checks in EOP).
- The SMTP AUTH Client Submission cannot send more than 10000 emails per day and more than 30 email per minute.
- Using SMTP AUTH Client Submission, the organization can send the emails to internal as well as external recipients.
- This method should be used when the organization wants to send emails outside the tenant but the MFD does not support Modern Authentication and only supports Basic Authentication.
- The email account used in MFD should be a Licensed user (should be a user mailbox) as shared mailbox will not work.
- TLS 1.2 should be used by the MFD
- If the MFD is sending the email using a static IP address then a valid spf record should be created for sending domain using the static IP address.
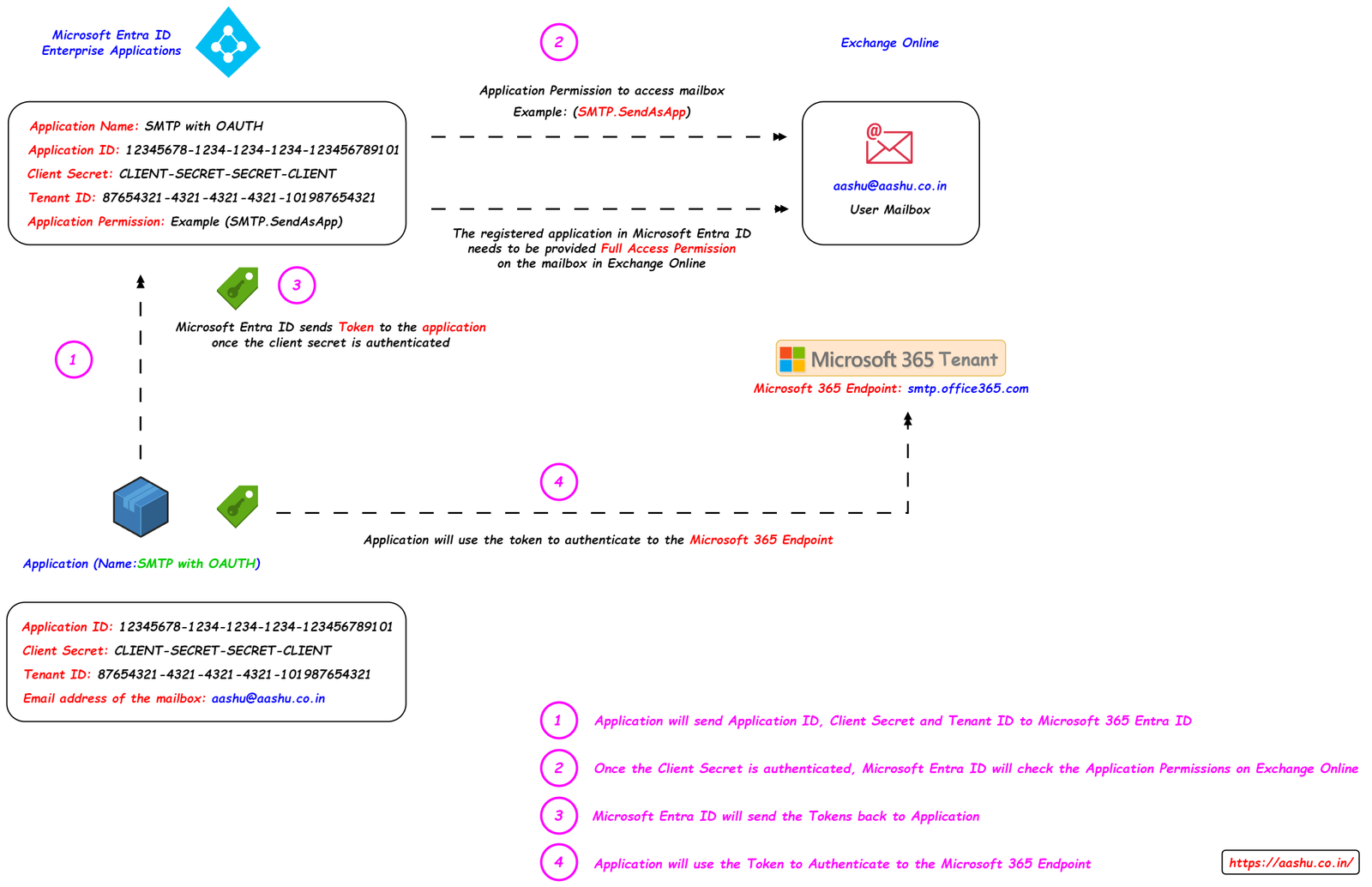
Method 2: IMAP, POP and SMTP with OAUTH (Modern Auth).
If the MFD or the organizations inhouse application supports OAUTH (Tokens or Certificates), then we can use this method to authenticate using Tokens or Certificates and then send emails using the application. There are few steps needed to be performed in Microsoft 365 if the application wants to use OAUTH to send emails instead of Basic Authentication.
Concept of using IMAP, POP and SMTP with OAUTH.
- We register the organization’s in-house or third party application in Microsoft Entra ID Enterprise Applications.
- Copy the Application ID, Client Secret and the Tenant ID of the registered application from the Enterprise Applications page.
- The registered application in Microsoft Entra ID needs to be provided Full Access Permission on the mailbox in Exchange Online.
- Use the Application ID, Client Secret and the Tenant ID in the in-house Application.
- Application will send the Application ID, Client Secret and the Tenant ID to Microsoft Entra ID.
- Microsoft Entra ID will authenticate the details sent by the application, and after that the application permissions will be checked on Exchange Online Mailbox.
- Microsoft Entra ID will send the Token to the Application.
- Application will use the Token to authenticate to Microsoft 365 Endpoint.
- Once the connection to the Microsoft 365 Endpoint will establish, the Application will send the email.
Method 3: High Volume Emails (Basic Auth and Modern Auth).
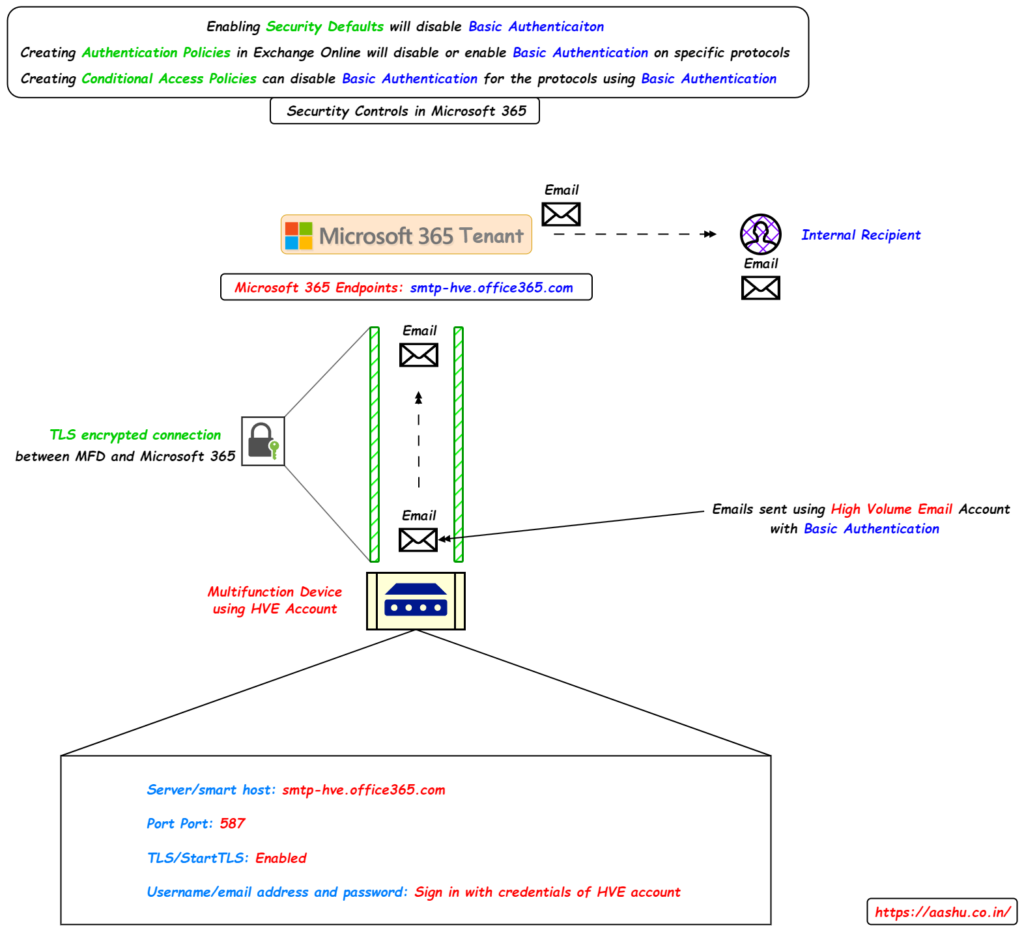
If your organization wants to send mass emails to internal users then we can go for High Volume Emails (HVE). HVE (currently in public preview and with general availability targeted for March 2026) can only send the emails to internal users. The basic authentication for HVE is supported until September 2028. In this method, Microsoft 365 creates a separate account (without a cloud-hosted mailbox), unlike SMTP AUTH. This HVE account uses Basic Authentication with SMTP protocol to send emails to internal users. The emails sent on HVE also bypasses most of the spam filters.
The advantage of using HVE is the organization gets to use Basic Authentication and Modern Authentication with MFD’s. If in case the HVE account gets compromised, the individual who gets the access to HVE account will not have any control over other workloads and admin centres in Microsoft 365, as HVE account is an isolated account provisioned just to send emails.
HVE supports both Basic Auth as well as Modern Auth
Below settings should be configured in MFD’s to use HVE method with Basic Auth.
- Server/smart host: smtp-hve.office365.com
- Port Port: 587
- TLS/StartTLS: Enabled
- Username/email address and password: Sign in with credentials of HVE account
High Volume Emails will fail if:
- Organization has enabled Security Defaults (which disables Basic Authentication).
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, the organization configuration does not allow this authentication request.
- Organization is using Conditional Access Policy to block the Basic Authentication.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, the organization configuration does not allow this authentication request.
- Organization is using Conditional Access Policy to apply Multi Factor Authentication.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful. Contact your administrator.
- The MFD is not using TLS 1.2 to encrypt the connection between MFD and Microsoft 365.
- Error: The server response was: 5.7.3 STARTTLS is required to send mail.
- If your organization is using trail subscription and does not have any purchased subscription for Exchange Online.
- Error: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 550 5.7.59 Trial tenant is not able to use HVE. Contact your administrator.
Key points to remember about HVE (with Basic Auth).
- Using HVE the organization can send emails to only internal recipients.
- The emails sent using HVE will bypass most of the spam checks in Microsoft 365.
- TLS 1.2 should be used by the MFD’s.
- Security Defaults, Conditional Access Policies should be disabled (to allow Basic Authentication)
- Authentication Policies should allow Basic Authentication.
High volume email (HVE) service is currently in public preview and subject to change.
In the next article Methods of Integrating Multifunction Devices with Microsoft 365 – Part 2, we will learn about the High Volume Email (with Modern Authentication), concept of Azure Communication Services (ACS), Direct Send and SMTP Relay method to send the emails using Microsoft 365.