In our previous article, we explored the types of security controls. This article is the Part 1 of the two part article which will cover the topic of “Summarize fundamental security concepts” in General Security Concepts domain for CompTIA Security + SY0-701 exam .
Table of contents
CIA Triad.
CIA stands for Confidentiality, Integrity, and Availability. CIA triad is the framework (model) used to build organization policies (Security Controls) to reduce the risk to organization data and assets. Organization’s security teams evaluates risk and vulnerabilities based on the potential impact they have on the confidentiality, integrity, and availability of an organization’s data and assets. After evaluation the security controls are implemented.
- Confidentiality focuses on keeping the organization data secret or private. It aims to protect the data from unauthorized access and sharing. Example: If a user is sharing any file over the network, and the file is not encrypted then the attacker may intercept the data. User may fail to protect the password to workstation or share the credentials with someone else, which in turn compromise the workstation and the organization’s data.
- To countermeasure Confidentiality organization must use the security controls like Firewall, Access Control List (ACL), Encryption, Labelling of data, strong passwords and multi-factor authentication (MFA) systems.
- Integrity focuses on maintaining the accuracy, reliability and completeness of data and making sure that the data is untampered, corrupted and trustworthy. Example: If an individual visits a website and if that website does not have a valid digital certificate then the individual will not trust the website (the data present in that website).
- To counter integrity, organization must use security controls like digital certificates authorities to protect websites, hashing algorithm like MD5 can be used to hash the data.
- Availability ensures that the data is available and accessible all the time so that the end user can access the data when needed. This means that the application, system and the network holding the data should be functional (up and running) at all times. Example: If a user is accessing the database on a server and there is power outage, making the server inaccessible.
- To ensure availability, organization can use security controls like backup and disaster recovery plans, DDOS protection.
DAD Triad.
DAD stands for Disclosure, Alteration and Denial/Destruction. The DAD triad explains threats to the CIA triad. It represents the attackers prospective and tactics to breach the CIA triad.
- Disclosure is unauthorized user gaining access to the organization’s data, that means sensitive data leaving the organization. Once the attacker get the access to the data, he can perform data transfer (Data exfiltration). Disclosure is a violation of the principle of confidentiality.
- Alteration is unauthorized modification of the data (changing the data from its original form). Attackers may modify the organizations financial records for their own financial gain. Alteration is the violation of the principle of integrity.
- Denial/Destruction is Preventing legitimate users from accessing the organization’s data and assets. Examples are DDoS attacks, ransomware and attacker deleting and rendering data inaccessible. Denial events violate the principle of availability.

Non-repudiation.
The concept of Non-repudiation ensures that the sender of message or the party which initiates the communication or transaction cannot deny the authenticity of the transaction or communication. This is achieved using access control, audit logging, timestamps and digital signature. Example: The sender uses digital certificate to sign the email, the sender cannot later deny that the email was not sent by him. Non-repudiation prevents someone from denying that they took an action.
Authentication, Authorization, and Accounting (AAA).
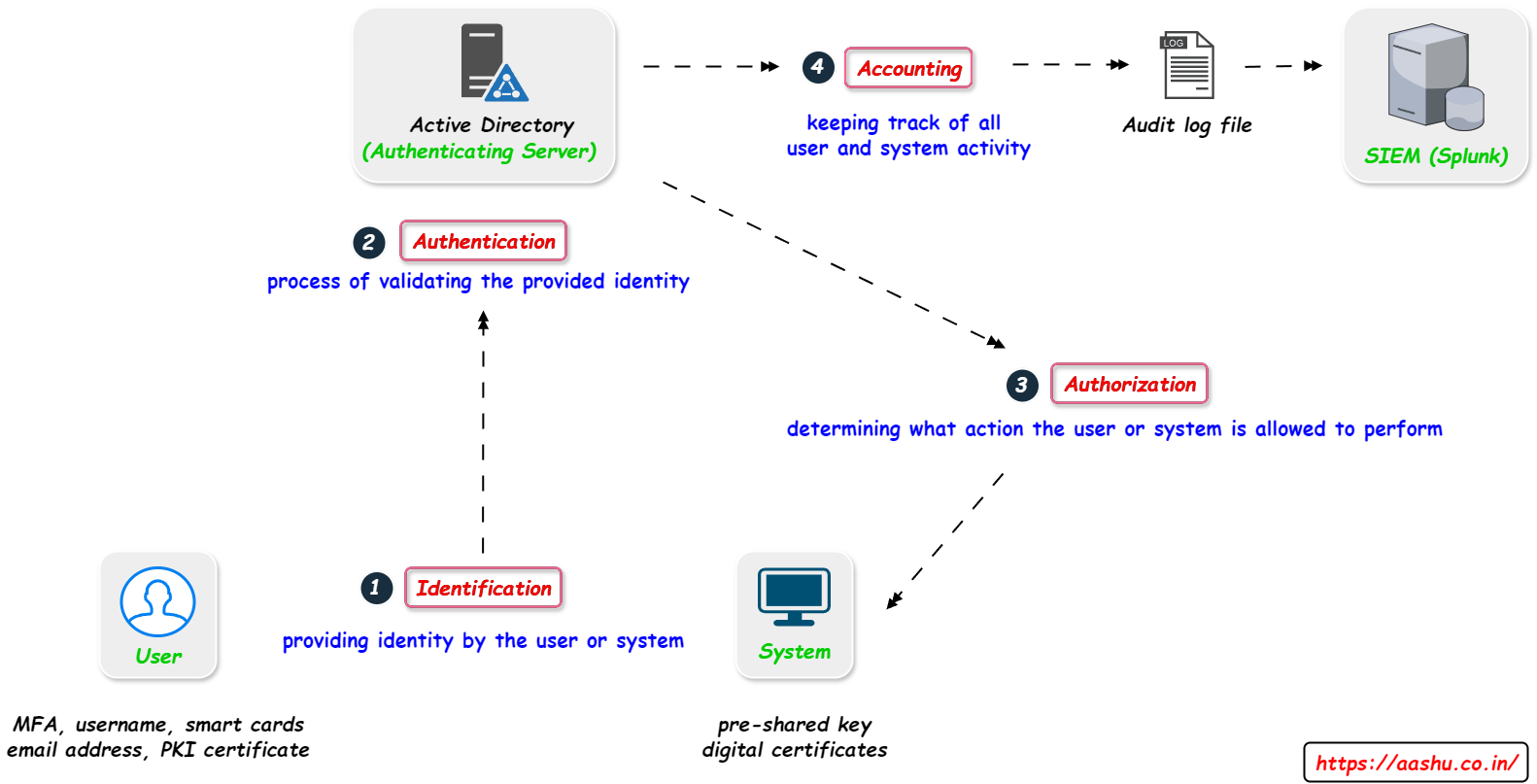
AAA is a framework in cybersecurity and network security that define the control access to the resources and monitoring user activities within system or network. AAA Servers are used in different network environments to ensure controlled access to the resources. Common example of AAA Server software are FreeRADIUS, TACACS+ server. AAA stands for Authentication, Authorization, and Accounting, but before Authentication there is Identification.
Identification.
Identification is the process when a user or system provides the identity to the Authenticating Server (example: Active Directory). Identification includes email address, username, digital certificate, fingerprint, MFA, pre-shared key, smartcard, or any other form of identification. It states who the user or system claims to be.
Authentication.
Authentication is the process of validating the provided identity. The Authenticating server compares the user or system provided identification and credentials with the credentials stored in the database. If credentials match then the user or system is authenticated, and if the credentials does not match, then the user or system is not authenticated. If authentication is successful then Authorization is checked.
- Authenticating People is process of identifying a user’s identity. Identification methods for a user are username, email address, PKI certificate, smart cards, MFA.
- Authenticating System is the process of identifying a system’s identity. Identification methods for a system are digital certificates, pre-shared key.
Authorization.
Authorization is the process of determining what action the user or system is allowed to perform or what resources the user or system is allowed to access. Authorization process comes after the successful authentication of the user or system. Authorization process makes sure that user have only the appropriate access privileges they need to do their job.
Accounting.
Accounting process keeps tracks of all the user or system activity for auditing and monitoring purpose. The logged data (audit logs) are stored securely making sure the integrity and confidentiality is not compromised. The audit data can later be retrieved for accounting or troubleshooting any issue and this data can also be sent to a real time monitoring system to generate compliance related reports.
Common AAA protocols.
There are various protocols used by AAA server for Authentication, Authorization and Accounting. The most widely used protocols by AAA server are RADIUS, TACACS+, and DIAMETER.
RADIUS.
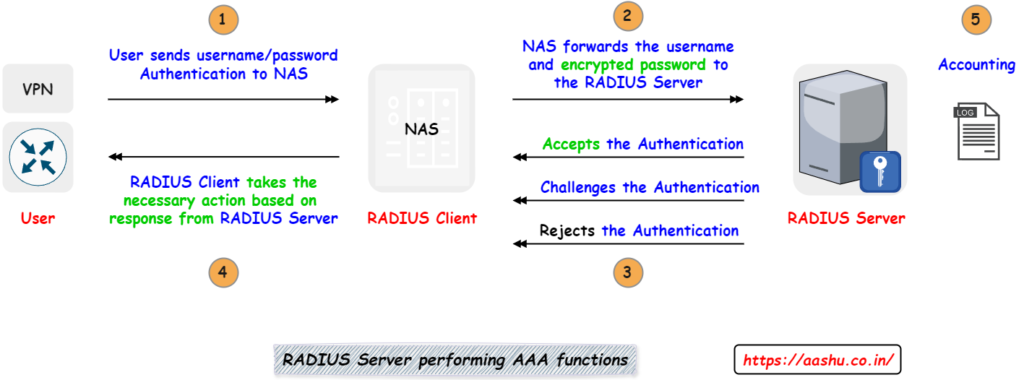
Remote Authentication Dial-In User Service (RADIUS) is a protocol used to authenticate, authorize and keep track of activities (accounting) for the users who wants to access the network or any resource on the network. RADIUS does AAA by using RADIUS Server and RADIUS Client. RADIUS Client is typically a Network Access Server (NAS) which is responsible of taking the username and password from the user and sending it to RADIUS Server. RADIUS Server is a daemon process on Windows or UNIX system. It is responsible for authenticating the user and return the details to the RADIUS Client. RADIUS uses UDP as a transport protocol. port 1812 is for authentication and authorization port, port 1813 is for accounting.
Process of AAA using RADIUS is mentioned below.
- User (Network devices, VPN’s) sends the authentication request (username/password) to RADIUS Client (Network Access Server (NAS)).
- NAS sends the username and encrypted password to RADIUS Server
- RADIUS Server will respond to the one of the below actions
- ACCEPT: Accepts the Authentication, access to the resource is granted.
- CHALLENGE: Challenges the Authentication, this is where the RADIUS Server needs more information before granting the access to the resource
- REJECT: User has failed to Authenticate, access to the resource is not granted.
- RADIUS Client acts on the response sent by RADIUS Server.
- RADIUS Server keeps track of activity (Accounting).
TACACS+.
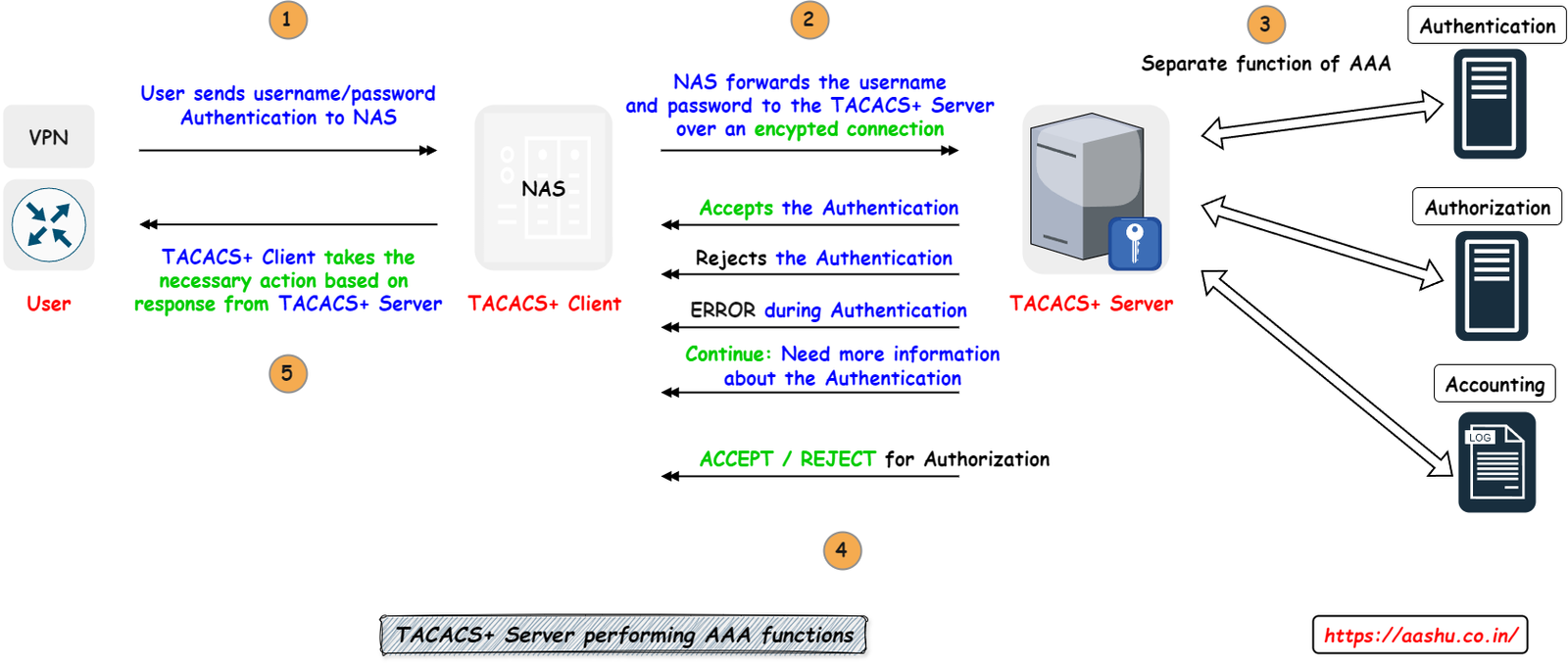
TACACS+ is a Cisco proprietary protocol, it provides AAA (Authentication, Authorization, and Accounting) services over a secure TCP connection using Port 49. TACACS+ uses Network access server (NAS) as TACACS+ client and TACACS+ Server. TACACS+ Server is a daemon process on Windows or UNIX system
TACACS+ Server can provide Authentication, Authorization and Accounting as a separate service. Each AAA functions can be configured, implemented, managed independently and can use a different database. Example: For Authentication, NAS can contact Active Directory and for Authorization and Accounting we can use TACACS + Server.
Process of AAA using TACACS+ is mentioned below.
- User (Network devices, VPN’s) sends the authentication request (username/password) to TACACS+ Client (Network Access Server (NAS)).
- NAS sends the username and password to TACACS+ Server over an encrypted connection.
- TACACS+ Server will respond to the one of the below actions
- ACCEPT: User is authenticated, the access to the resource or service is granted, if NAS is configured to send authorization request, then the authorization request will be received.
- REJECT: User failed to authenticate and the access to the resource or service is not granted.
- ERROR: an error occurred at the time of authentication.
- CONTINUE: requires more information about authentication from the user.
- If Authorization request is received, the TACACS+ Server will send the ACCEPT or REJECT authorization response.
- TACACS+ Client acts on the response sent by TACACS+ Server.
- TACACS+ Server keeps track of activity (Accounting).
The advantage of TACACS+ over RADIUS is that the connection between TACACS+ Server and TACACS+ Client is encrypted and hence all the data between the two will be sent over encrypted channel (unlike RADUIS where only the password will be encrypted and sent to RADIUS Server). TACACS+ uses TCP at as a transport protocol ensuring reliable connection between Server and Client.
Diameter.
Diameter protocol is used for AAA in Telecommunication, data mobility applications and in modern network. Example 4G, 5G networks, voice, video, and messaging services. It uses TCP (transmission Control Protocol) and SCTP (Stream Control Transmission Protocol) for reliable connection.
Gap Analysis.
Gap analysis is the process of evaluating or assessing an organizations current security practices against the industry standard best practises. The Gap analysis process compares the existing security controls, policies, and procedures to the best practices and security standards, this identifies the discrepancies and gaps in the current security posture. By conducting a gap analysis assessments, the organization can identify the risks and improve the security practices.
Below are the steps in Gap Analysis assessment.
- Define Objectives & Scope of the assessment: Purpose of gap analysis like focusing on specific systems, processes or compliance requirements.
- Select an industry-standard security framework: Select the security framework like CIS Control, NIST Cybersecurity Framework.
- Assess the Current Security Posture: Review security policies and procedures, Conduct vulnerability assessments and penetration testing.
- Identification of Gaps: Compare the current security state with the selected industry-standard security framework.
- Prioritization of Gaps: Prioritize the Gaps based on potential impact and the level or risk.
- Development of Remediation Plan: Develop a detailed Remediation strategy to close the identified Gaps.
In the next article, we will cover the topic Zero Trust, Physical security and Deception and disruption technology.