in the previous article Summarize fundamental security concepts Part 1 we have explored the concepts of CIA and DAD triad, Non-repudiation, Authentication, Authorization, and Accounting (AAA) and Gap Analysis. In this article we will focus on few other fundamental security concepts.
Table of contents
Zero trust.
Zero Trust architecture is a cybersecurity framework that works on the principle “never trust, always verify”. The basic principle is not to trust anything by default and access should be provided by validating the legitimacy of users and devices accessing resources, regardless of their location. Zero Trust architecture is divided into Control plane and Data plane.
Control Plane.
Control Plane manages the intelligence behind the data routing, AAA and other security control enforcement. It also helps with continuous verification of users and devices, ensuring they receive only the minimum necessary access to the organization’s resources. The control plane uses the below methods and strategies to manage security policies across an organization’s network, applications, and resources.
Adaptive Identity.
Adaptive identity model refers to dynamically adjusting the authentication, access and permission requirements based on user identities, real-time risk assessments and contextual data like identity behaviour, user location, or device characteristics of the user, who is trying to authenticate. After analysing all the details related to user authentication, an intelligent access decision is made which is aligned with the organization’s security posture.
Example: A user wants to access the company resource (email) from a public Wi-Fi, then the Adaptive Identity model will check the user location or device (untrusted location / device – outside the organization), analyses the risk associated with the authentication, and based on the security policies the Adaptive Identity model will prompt for additional user authentication (MFA) or to use VPN and then the access to the organization resource (email) will be allowed.
Threat Scope Reduction.
Threat scope reduction refers to the practice of minimizing the potential attack scope and limiting the potential damage a threat can inflict on an organization, ultimately reducing the impact of a security breach. Below are the strategies used to reduce the threat scope.
- Network Segmentation: breaking the network into smaller, isolated and controlled segments for more access control. This limits the lateral movement of the attacker.
- Least Privilege Access Control: enforcing access controls based on the principle of least privilege.
- Device Health Checks with security patch management.
- Application Allowlisting: allowing only the approved application on the organization network.
- Continuous Monitoring and Threat Detection: using endpoint detection and response (EDR) and security information and event management (SIEM) system to monitor and track unusual behaviour in the organization network and resources.
Policy-driven Access Control.
As the name suggests, user or device will be grated or denied the access to the network resources based on predefined security policies. This involves creating specific rules (policies) that manages access to network resources. These policies determine who can access which resources, when, and with what permissions.”. The predefined security policies are written by organization’s security team.
Policy Engine.
Policy Engine makes the decision of who can access the network resources based on predefined security policies and input from external sources (like SIEM, threat intelligence, Activity logs, Continuous Monitoring Systems). Once the policy engine evaluates all the parameters, it communicates its decision to a policy administrator, who executes the decision.
Policy Administrator.
The policy administrator executes the decisions made by the policy engine. They issue access tokens and can communicate with the data plane.

Data Plane.
Data Plane (or Forwarding Plane) is responsible for movement of data packets within the network. This is where the decision from control plane is enforced and the data packets are inspected, routed, blocked, modified or allowed based on the security policies. The Data Plane uses the below strategies to enforce the policy decisions.
Subject/System.
Subject refers to the user, device or process seeking access to the resources on the network. Subjects are authenticated and authorized before they access the resource. System is a collective term for resources, infrastructure or devices which is responsible for processing and forwarding of data packets in the organization network.
Implicit trust zones.
Implicit trust zones refers to an area in the organization network where the entities (users, devices) are trusted and granted certain privileges without continuous verification. The concept of Implicit trust zones directly violates the Zero Trust security framework. Implicit trust zones were used in traditional security models, in Zero Trust framework, the concept of implicit trust zones is eliminated.
Policy Enforcement Point.
Policy Enforcement Point responsible for allowing or blocking the access to the resource based on the decision of policy engine. The Policy Enforcement Point communicates with the Policy Administrator to forward requests and/or receive policy updates from the Policy Administrator.
Basic assumptions of Zero Trust.
Zero Trust is based on below basic assumptions.
- No Implicit Trust Zone: No user or network should be automatically trusted and granted access to the resource. All the access request should be authenticated and authorized based on predefined security policies.
- Continuous Verification: (Authentication and Authorization) Access to the resource is granted on per session basis and it must be re-evaluated.
- Least privilege access: Entities trying to access the resource on the network should be granted only the minimum access required to perform their functions.
- Continuous Monitoring: All network activities should b continuously monitored to detect and respond to any anomaly in real-time.
- Assume breach: Always operate under the assumption that a breach has already occurred.
Physical security.
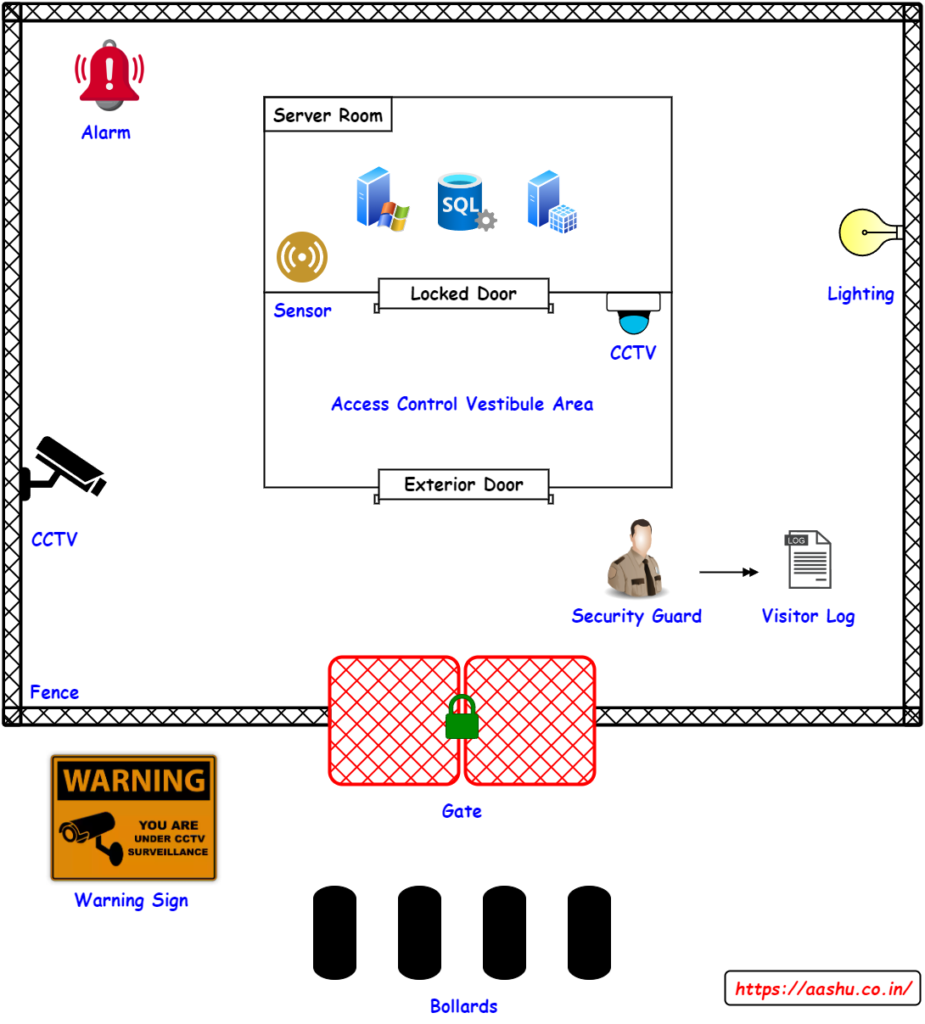
Physical security refers to physically protecting the organization assets (buildings, equipment, personnel) from damage, theft or unauthorized access. it uses different practice, procedures and equipment to protect the organization owned assets. Below are few of the physical security measures and organization can take to protect the organization asset.
- Bollards: A bollard is a short post used to create a protective perimeter and control vehicle access. Bollards can be Fixed, such as concrete bollards to permanently prevent the passage of vehicles. Removable bollards, Semi-automatic or Automatic bollards are operated by an access control systems, allowing authorised vehicles to pass through whenever required.
- Fencing wire: It is a durable metal wire used to create barrier or boundaries.
- Automatic or manual Gates can be used with Fencing to allow authorized users.
- Organization can post warning signs to communicate rules, regulations, and warnings to discourage unauthorized access and prevent trespassing.
- Access control vestibule consists of a small space and two interlocking doors. One set of the doors must close before the other one can be opened so that an individual is briefly ‘trapped’ in the vestibule before clearing the second door. These vestibules can be manually operated or have automatic systems.
- Security Guard is an individual employed by an organization to protect organization assets from various security threats.
- Visitor logs are records that track the entry and exit of visitors in the organization. Visitor logs can be manual (stored on paper) or digital (stored digitally).
- Video Surveillance uses Security Cameras to monitor and record what is happening within the cameras’ field of view. It provides real-time visibility and a historical record of events.
- Badge Access Control System is an automated security solution which allows entry to only authorized individuals using electronic badges or key cards. When someone scans their badge at a reader, the system verifies their access. If they’re authorized, the door unlocks. If not, access is denied.
- Lighting inside and outside a organization building serves multiple purpose. It will discourage the intruder, it enhances visibility by reducing hiding spots.
- Sensors enhance physical security in an organization by detecting and responding to potential threats or unauthorized activities. Below are the types of sensors.
- Infrared sensors detect and measure infrared radiation emitted or reflected by objects in their field of view. They are commonly used in physical security systems to detect movement and trigger alarms. Example: motion detectors, fire detector sensor.
- Pressure sensors are devices that detect changes in pressure to identify potential threats or intrusions Example: Pressure-Sensitive Mats (Under-carpet, Mat Sensors) are placed in restricted zones to detect when someone steps on them.
- Microwave sensors emits microwave pulses and detects frequency alterations caused by moving objects, when movement is detected, the sensor triggers an alarm. Example: Vehicle Detection, Monitoring for unauthorized access in Servers rooms.
- Ultrasonic sensors uses ultrasonic sound waves to detect the presence, movement, or proximity of objects or individuals. These sensors emit Ultrasound waves, detects and measures the sound waves bounce off objects in their path and triggers the alarm.
Deception and Disruption Techniques.
Deception techniques are used to misleads the attacker to attack a decoy system that mimics the organizations legitimate asset. The decoy system will keep the attacker busy and this allows the security teams to monitor and analyse their behaviour of the attack. Once an attacker interacts with a decoy, disruption techniques are used to slow the progress of the attacker diverting their attention away from real assets. Below are the deception and disruption techniques.
Honeypot: A single decoy system or server designed to attract and trap attackers mimicking a legitimate resource. When the attack attacks the Honeypot considering it as a legitimate resource, the security team monitors the attack methods so that they can prevent future attacks. Example: A decoy database server filled with dummy data that mimics the structure of a genuine data.
Honeynet: A network of interconnected honeypots. Hoenynet simulate a more realistic and complex environment for attackers to explore which mimics the organization’s real network. Example: A virtual network consisting of dummy servers, and client systems.
Honeyfile: A decoy file or document placed within a system to lure attackers. as per attackers perspective, these file contains valuable information. Example: file named “password.txt” saved on computer. Honeyfile can be used to check more details about who accessed the file.
Honeytoken: It is a dummy data with a marker (unique identifier). Once the dummy file is accessed, used, or moved, it triggers an alert, this information can be used to track the attacker.